51 lines
2.9 KiB
Markdown
51 lines
2.9 KiB
Markdown
|
|
## CAPA
|
|||
|
|
|
|||
|
|
**CAPA** detects capabilities in executable files. May it be for the installation of a service, invocation of network connections, registry modifications and such.
|
|||
|
|
|
|||
|
|
To start playing with CAPA, fire up the command prompt located in the taskbar and navigate to the Malware Sample directory, as shown below.
|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|
```cmd
|
|||
|
|
C:\Users\Administrator>cd "Desktop\Malware Sample"
|
|||
|
|
C:\Users\Administrator\Desktop\Malware Sample>capa mysterygift
|
|||
|
|
loading : 100%|████████████████████████████████████████████████████████████| 485/485 [00:00<00:00, 1633.69 rules/s]
|
|||
|
|
matching: 100%|██████████████████████████████████████████████████████████████████| 3/3 [00:02<00:00, 1.11 functions/s]
|
|||
|
|
WARNING:capa:--------------------------------------------------------------------------------
|
|||
|
|
WARNING:capa: This sample appears to be packed.
|
|||
|
|
WARNING:capa:
|
|||
|
|
WARNING:capa: Packed samples have often been obfuscated to hide their logic.
|
|||
|
|
WARNING:capa: capa cannot handle obfuscation well. This means the results may be misleading or incomplete.
|
|||
|
|
WARNING:capa: If possible, you should try to unpack this input file before analyzing it with capa.
|
|||
|
|
WARNING:capa:
|
|||
|
|
WARNING:capa: Use -v or -vv if you really want to see the capabilities identified by capa.
|
|||
|
|
WARNING:capa:--------------------------------------------------------------------------------
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
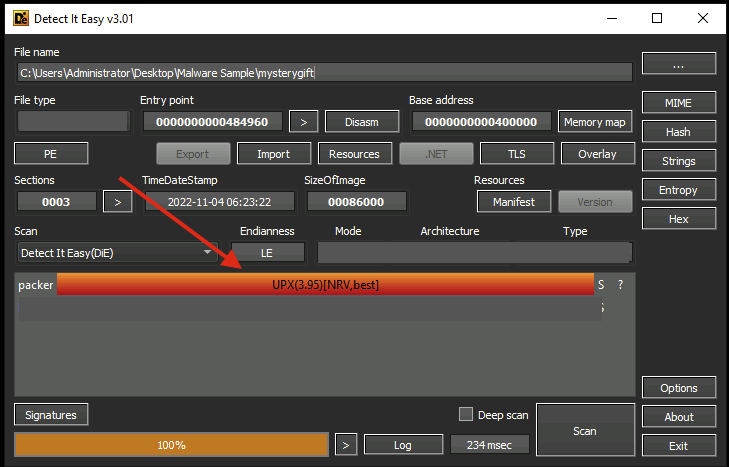
Given the CAPA output, we have discovered that the malware sample is packed. You may have also seen previously from **Detect It Easy** that the binary is packed by UPX.
|
|||
|
|
|
|||
|
|
|
|||
|
|
|
|||
|
|
So now, let's unpack the binary using UPX and re-analyse the binaries using CAPA.
|
|||
|
|
|
|||
|
|
```cmd
|
|||
|
|
C:\Users\Administrator\Desktop\Malware Sample>upx -d mysterygift
|
|||
|
|
Ultimate Packer for eXecutables
|
|||
|
|
Copyright (C) 1996 - 2020
|
|||
|
|
UPX 3.96w Markus Oberhumer, Laszlo Molnar & John Reiser Jan 23rd 2020
|
|||
|
|
|
|||
|
|
File size Ratio Format Name
|
|||
|
|
-------------------- ------ ----------- -----------
|
|||
|
|
502169 <- 227737 45.35% win64/pe mysterygift
|
|||
|
|
|
|||
|
|
Unpacked 1 file.
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
```cmd
|
|||
|
|
C:\Users\Administrator\Desktop\Malware Sample>del mysterygift.viv
|
|||
|
|
C:\Users\Administrator\Desktop\Malware Sample>capa mysterygift
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
- You may observe that CAPA now has provided important information about the malware sample.
|
|||
|
|
|
|||
|
|
Note: We have executed `del mysterygift.viv` to delete the cached results of the first CAPA execution. By deleting the viv file, CAPA re-analyses the binary with accurate results.
|